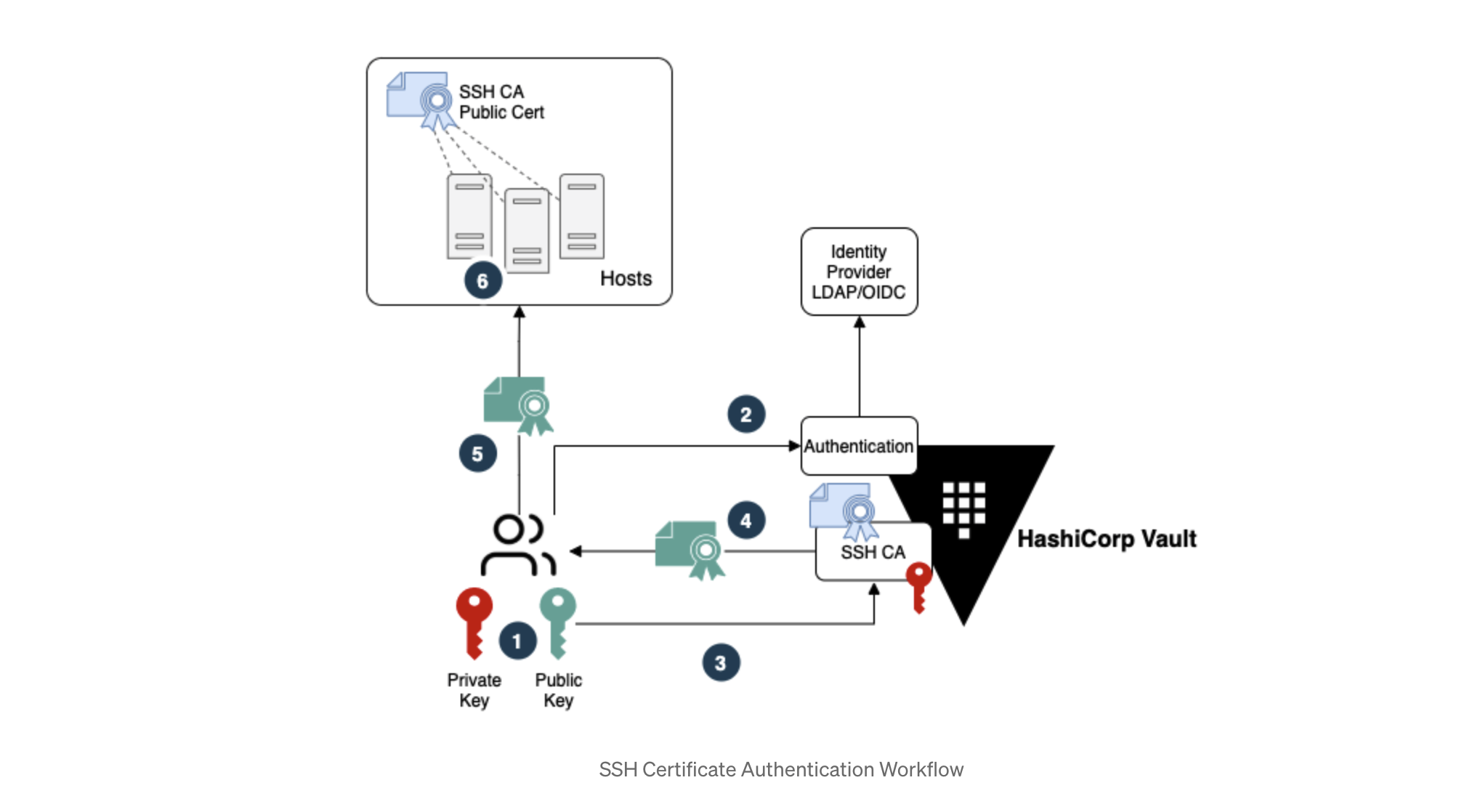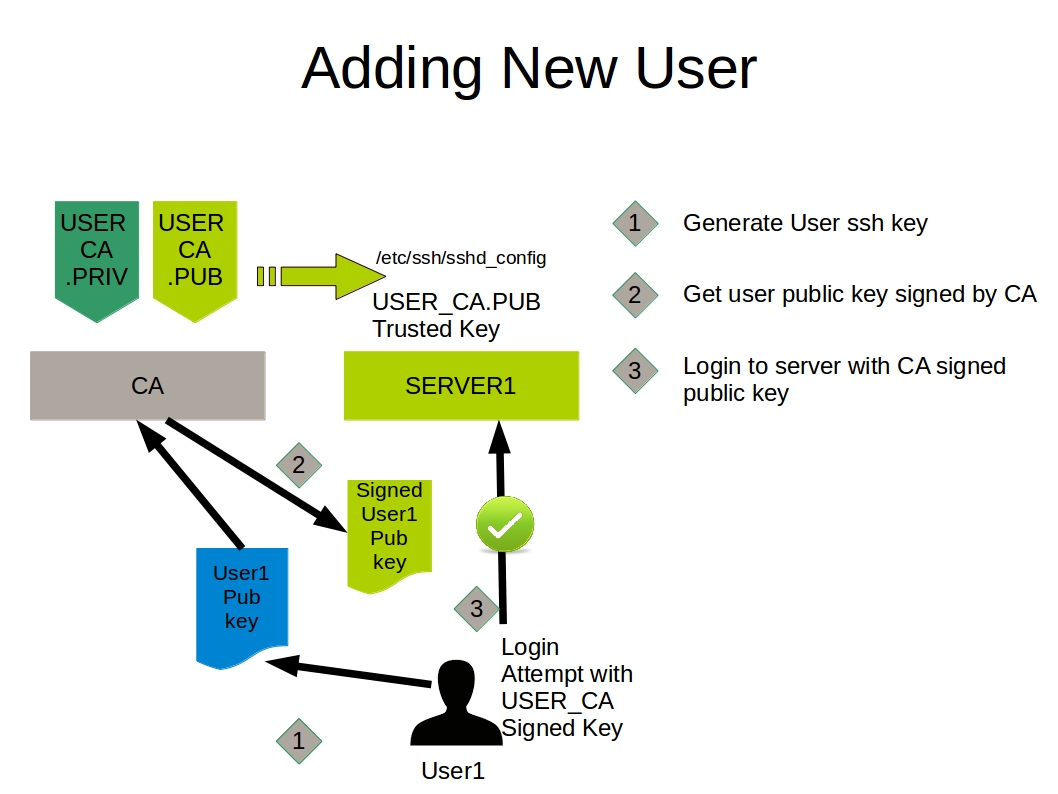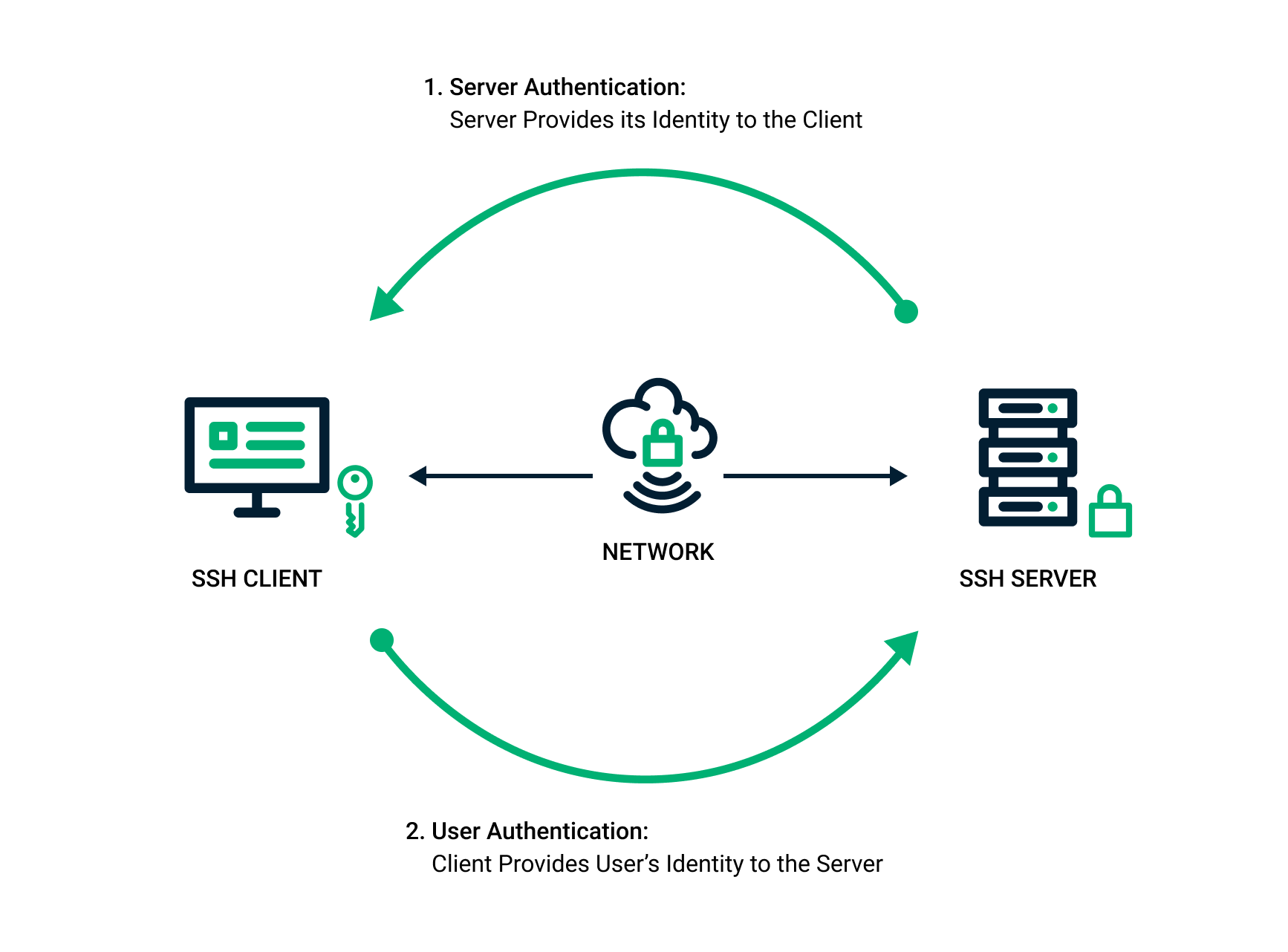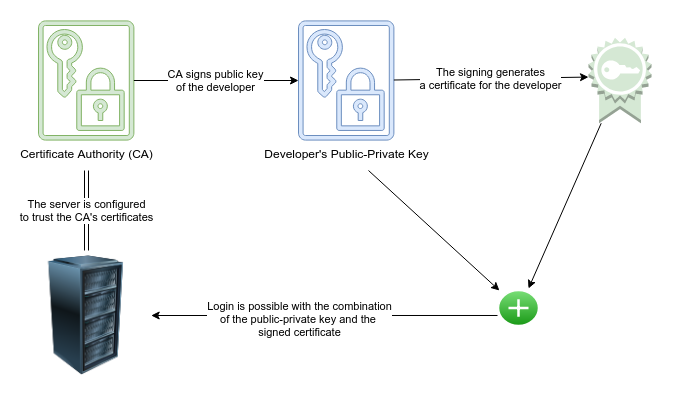
How to properly manage ssh keys for server access :: Päpper's Machine Learning Blog — This blog features state of the art applications in machine learning with a lot of PyTorch samples

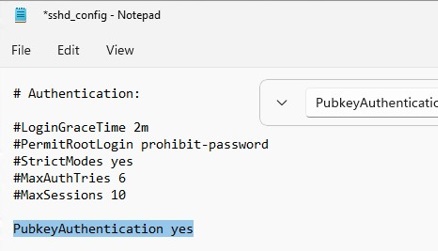
The private key verification file /etc/ssh/sshd_config private key - aaPanel - Free and Open source Hosting control panel. One-click LAMP/LEMP.