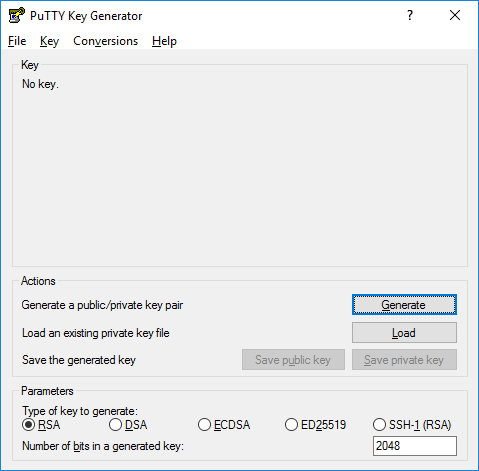
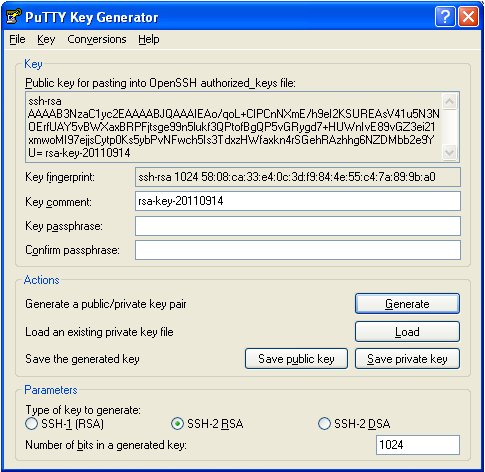
A New Method IBE Interfaced with Private Key Generation and Public Key Infrastructure to Achieve High Data Security | Semantic Scholar
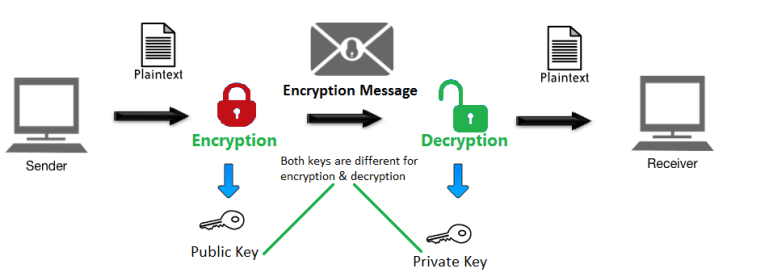
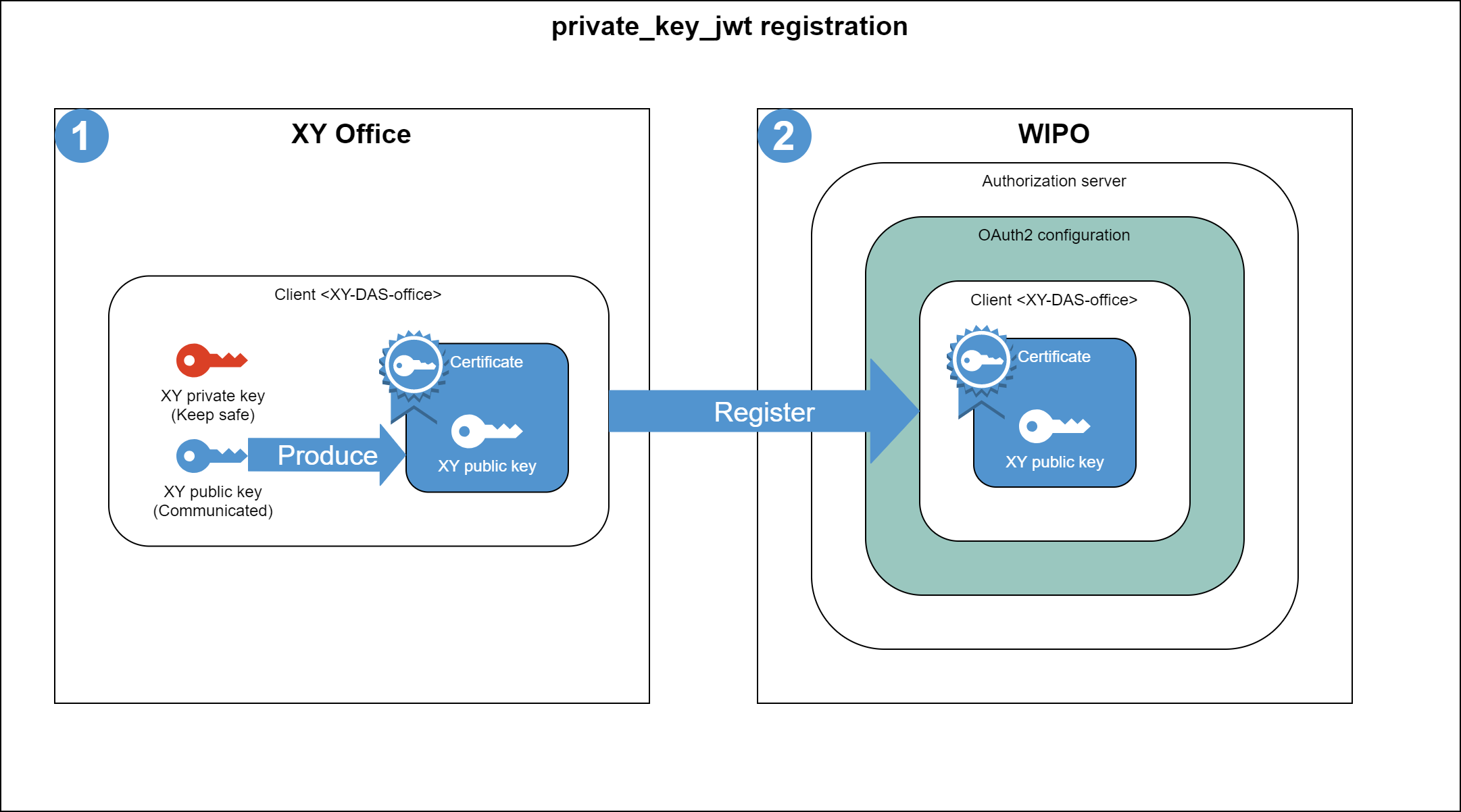
The public and private key pair generation by the receiving party III.... | Download Scientific Diagram
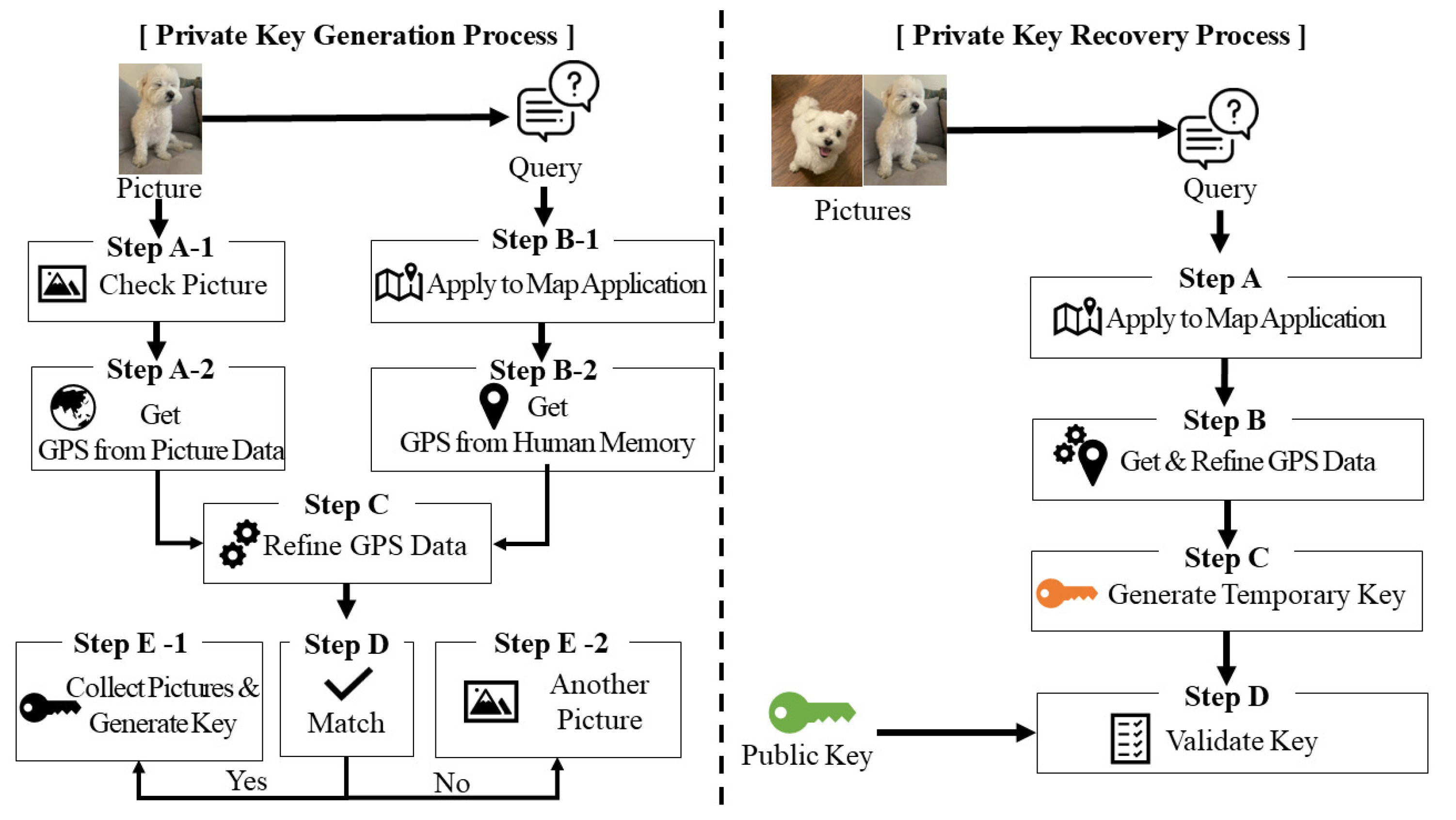
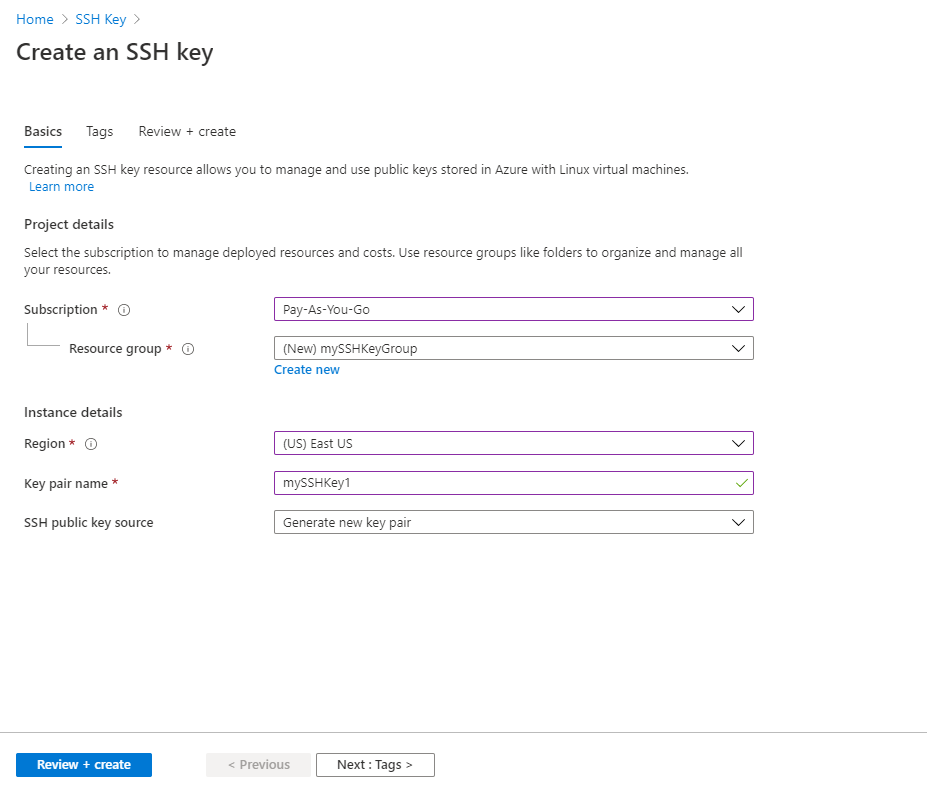
Mathematics | Free Full-Text | Reminisce: Blockchain Private Key Generation and Recovery Using Distinctive Pictures-Based Personal Memory