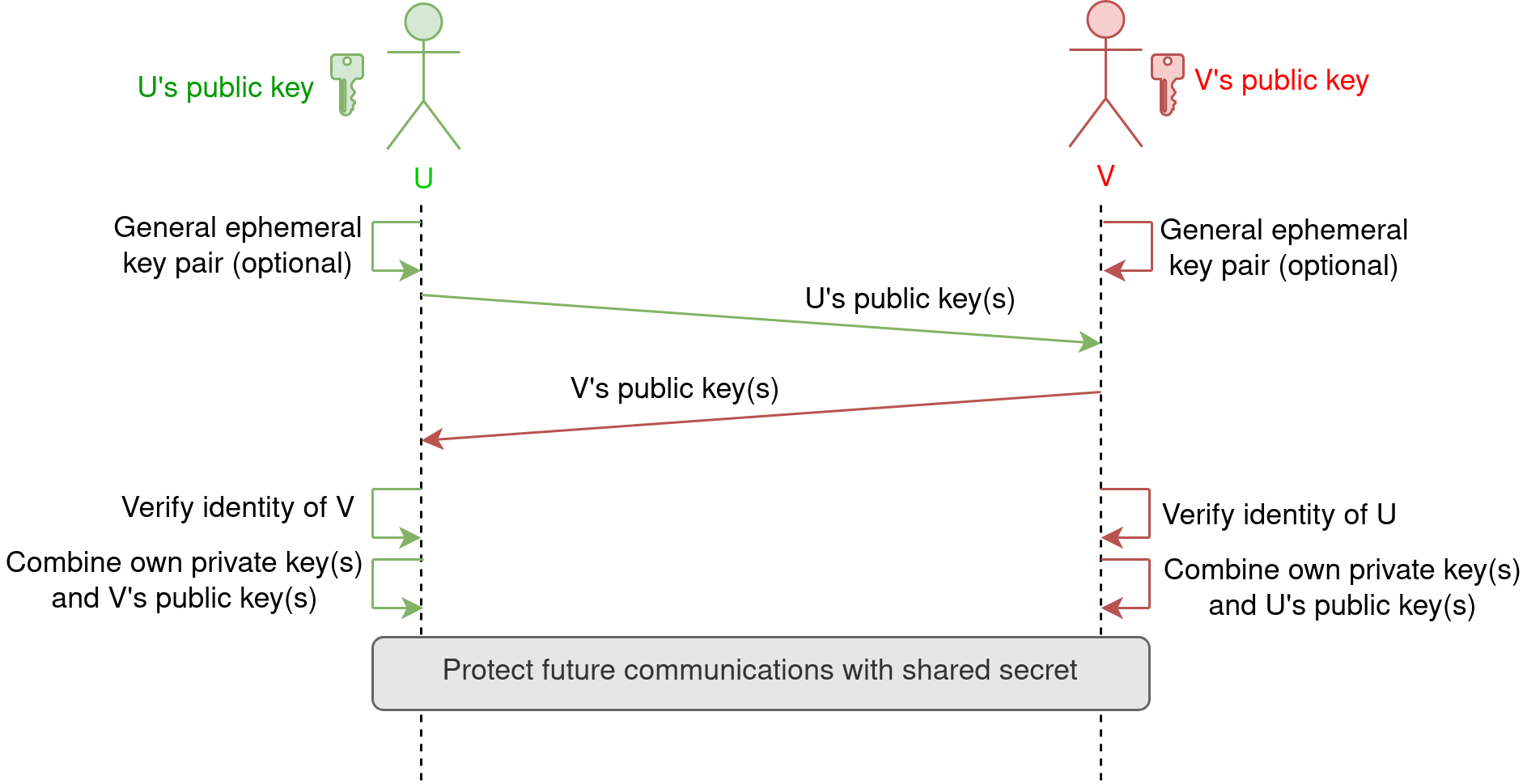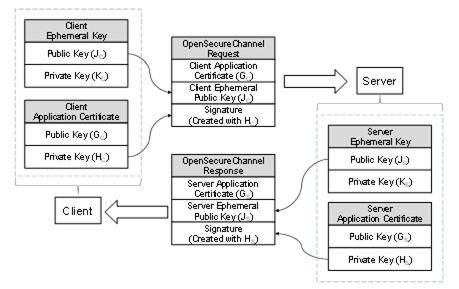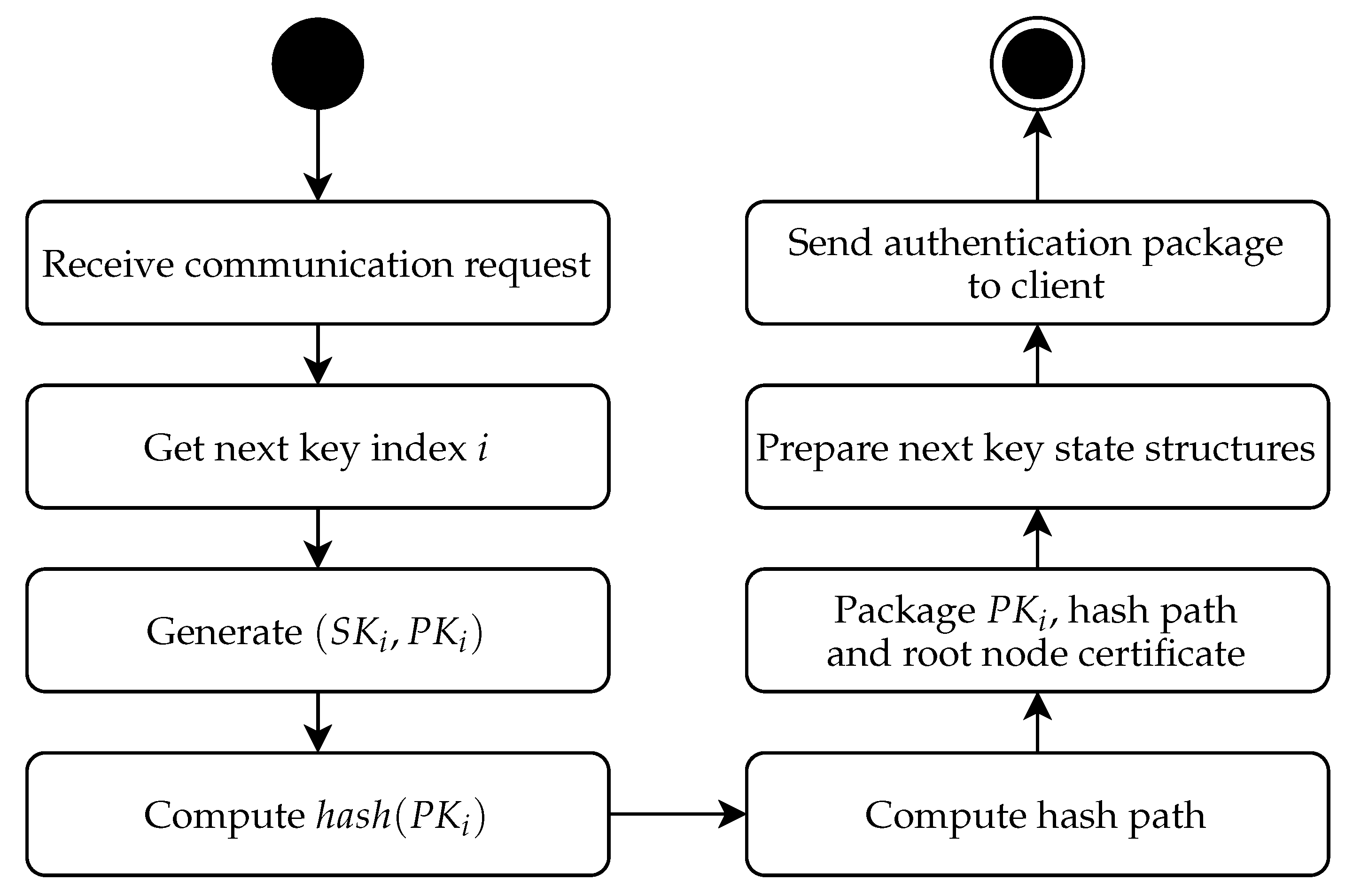
Sensors | Free Full-Text | Ephemeral Keys Authenticated with Merkle Trees and Their Use in IoT Applications
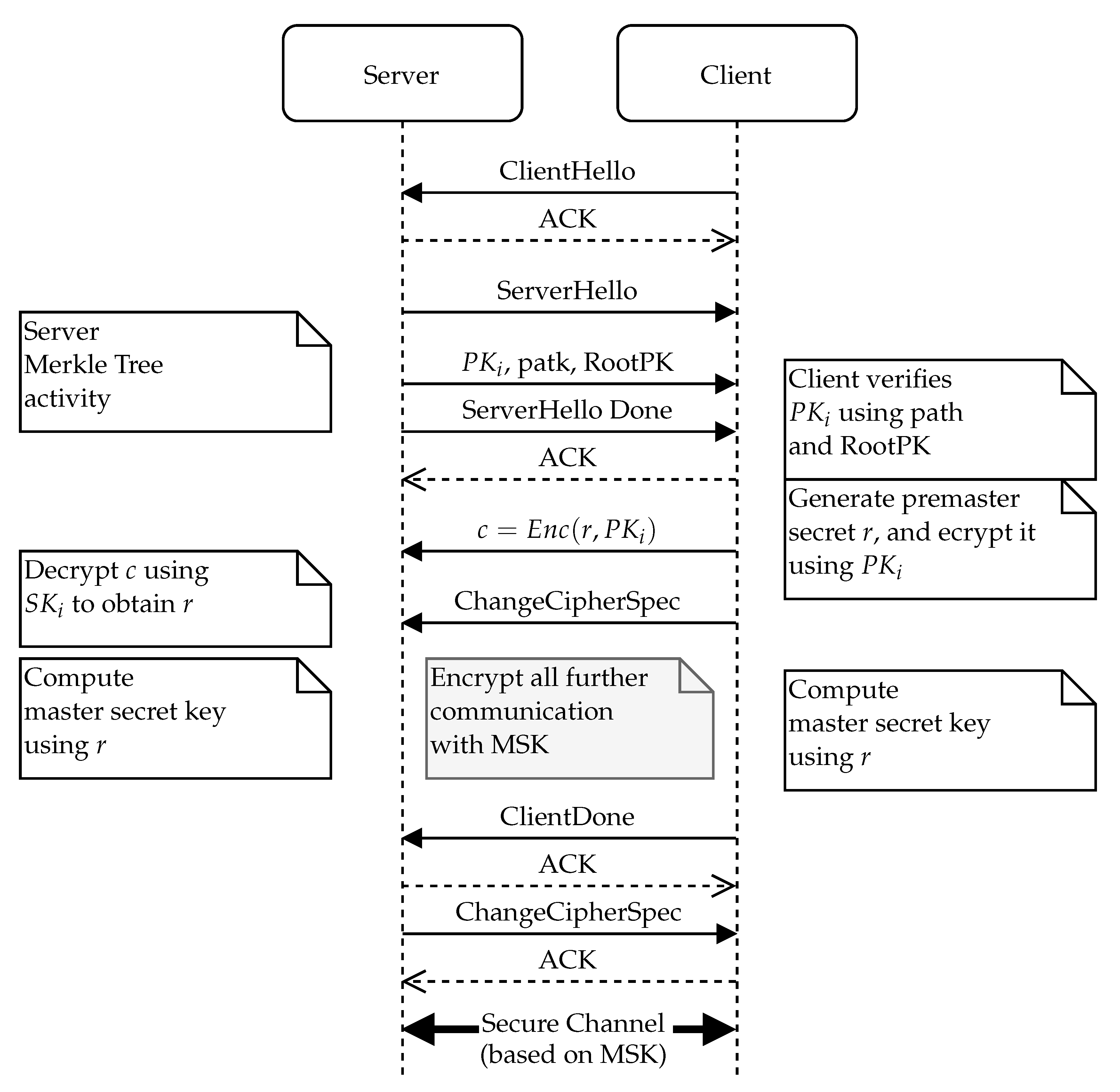
Sensors | Free Full-Text | Ephemeral Keys Authenticated with Merkle Trees and Their Use in IoT Applications

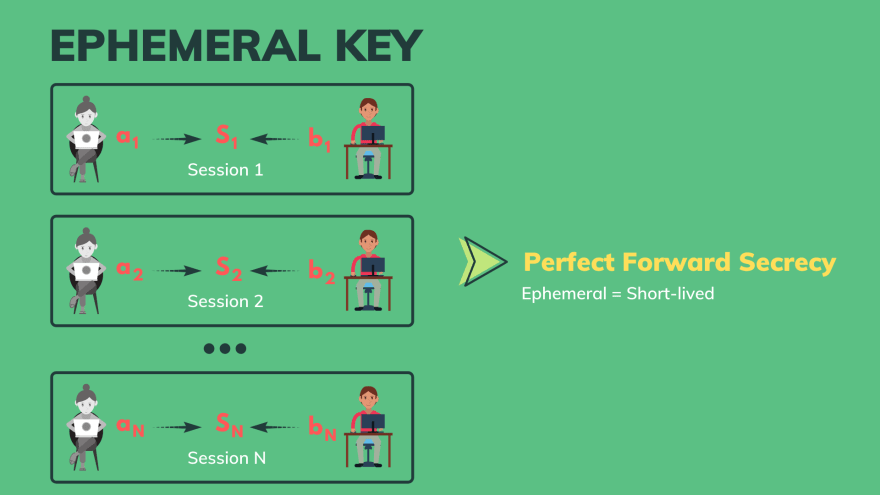
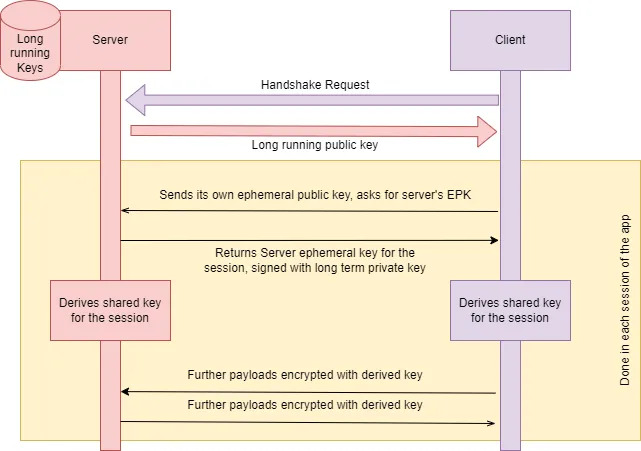
vixentael 🛡🇺🇦 on X: "Save to read later: SSL pinning, ephemeral keys explained https://t.co/MB5AdJvwt8 #appbuilders16 https://t.co/CUzRf2aRAb" / X

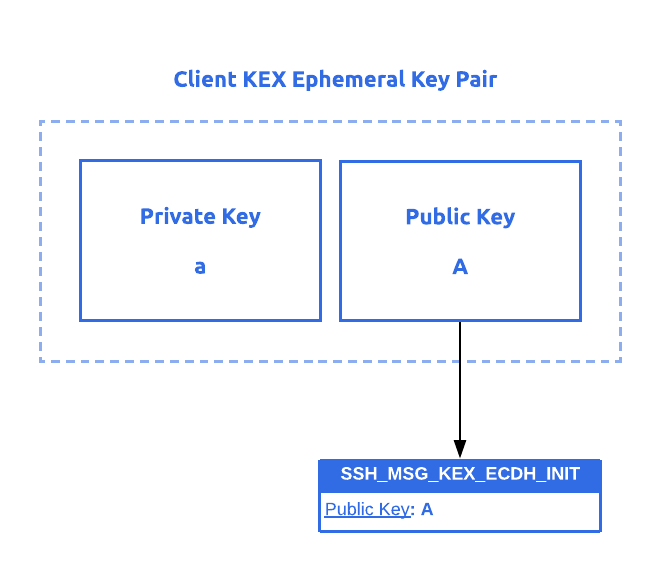

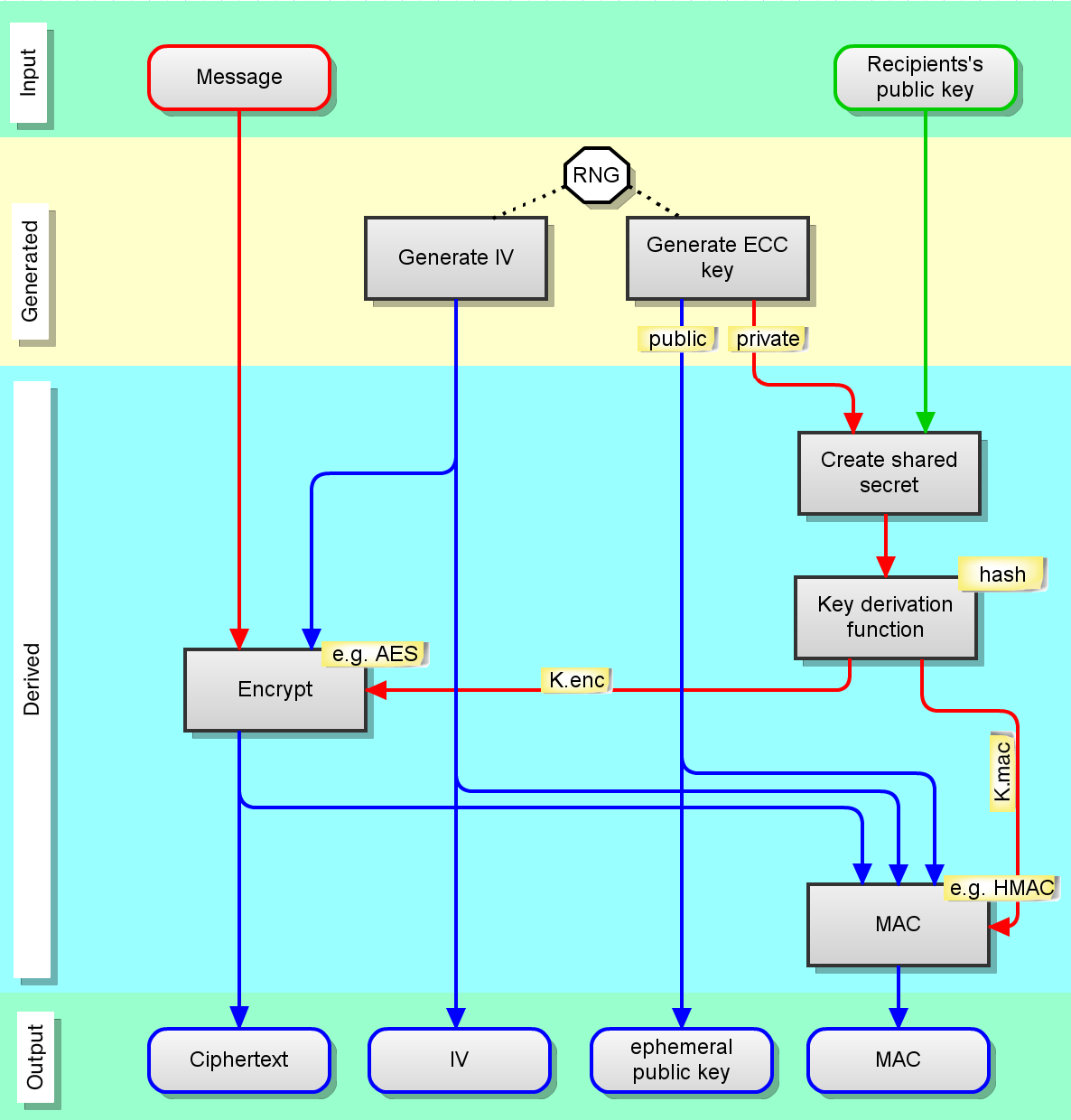
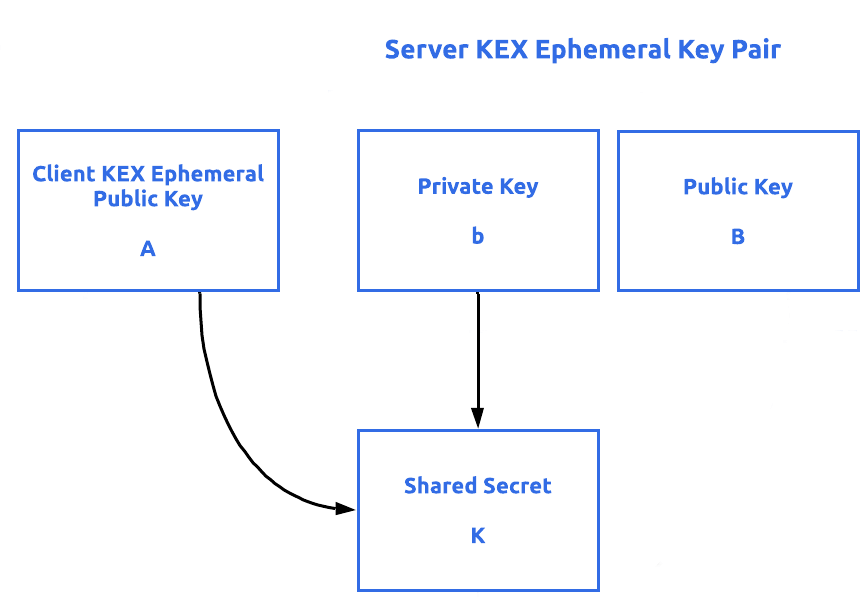

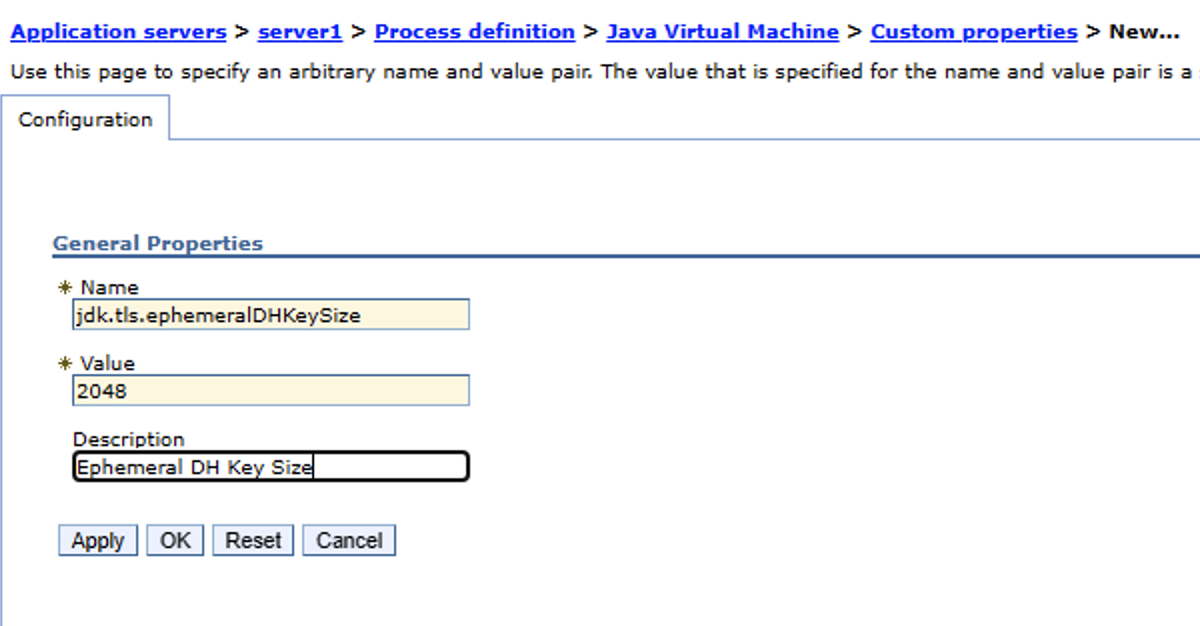



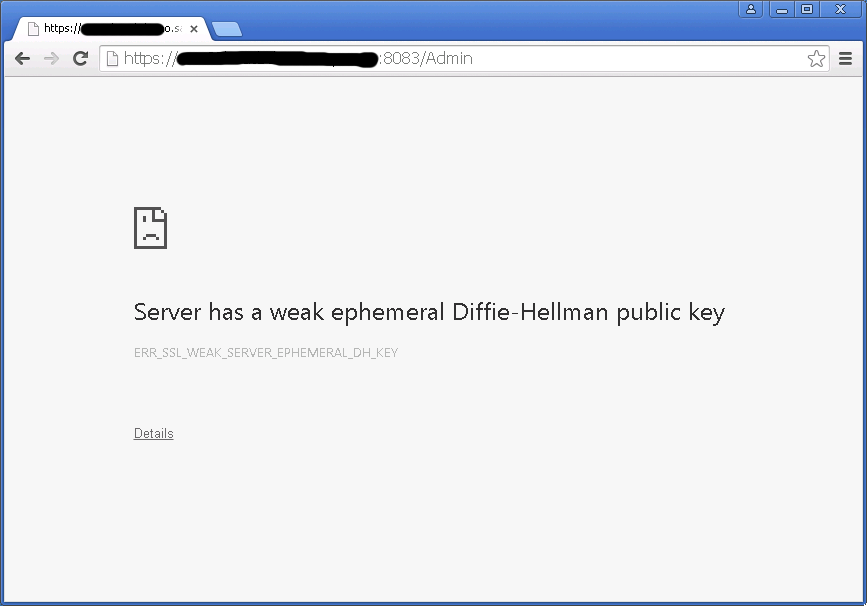

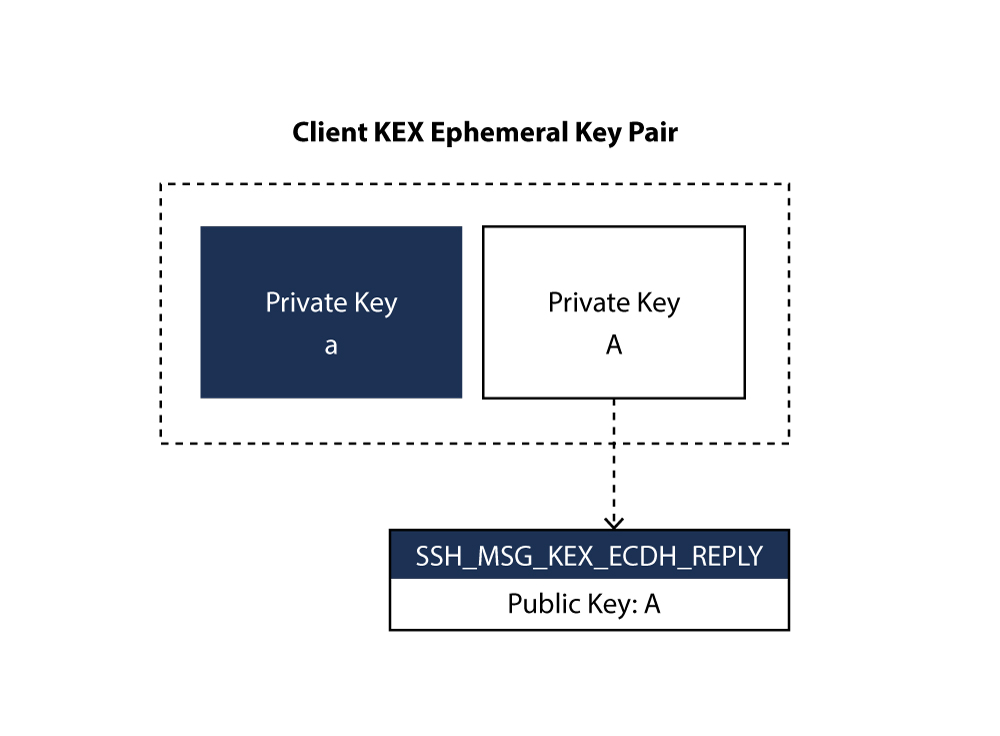

![BUG] using expired Ephemeral Key · Issue #6532 · stripe/stripe-android · GitHub BUG] using expired Ephemeral Key · Issue #6532 · stripe/stripe-android · GitHub](https://user-images.githubusercontent.com/6266608/231778740-66f998ad-6073-4230-859c-14ba033c7e17.jpeg)