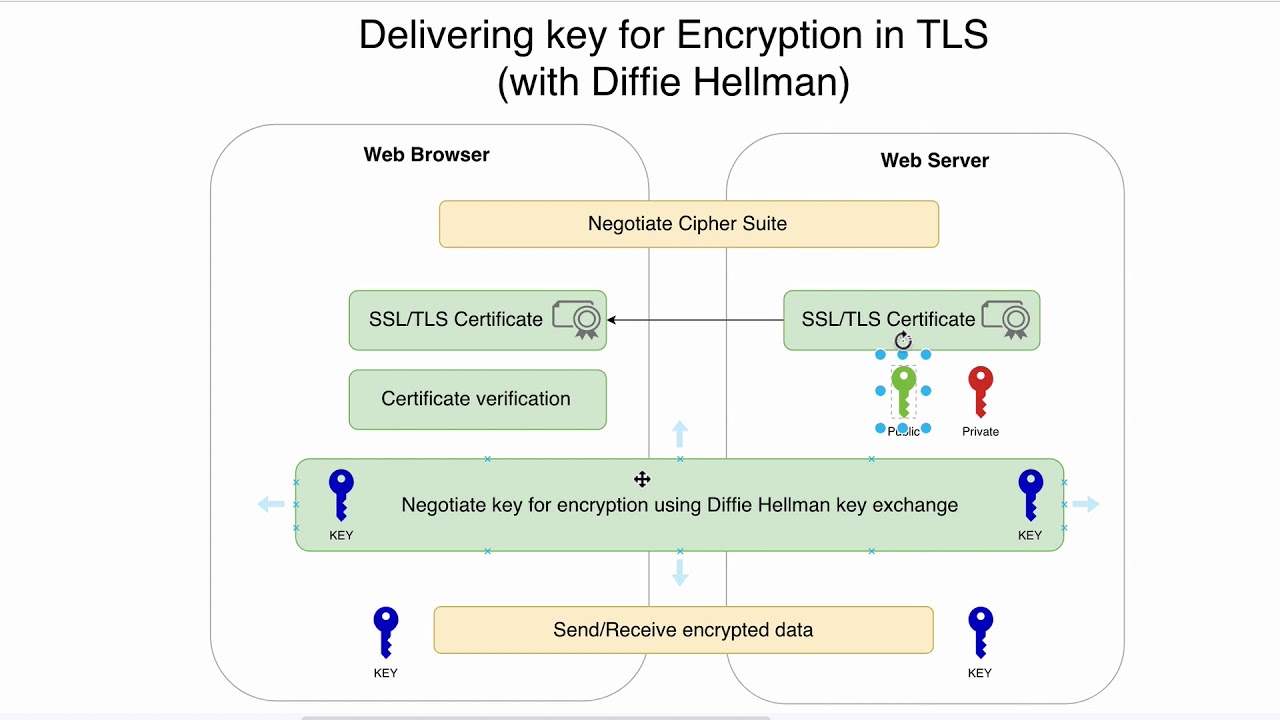
Sahn Lam on X: "How does HTTPS work? Hypertext Transfer Protocol Secure (HTTPS) is an extension of HTTP that utilizes Transport Layer Security (TLS) to encrypt communication between a client and server.
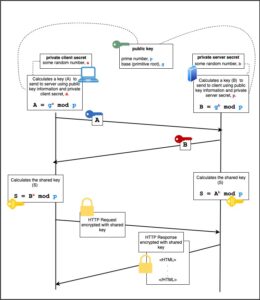
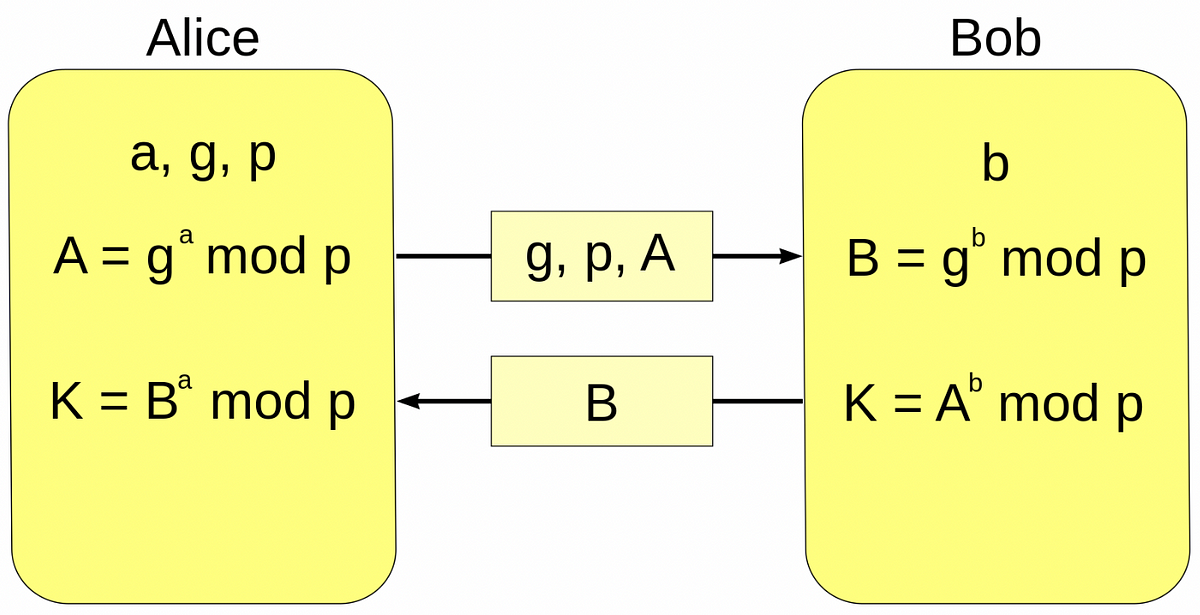
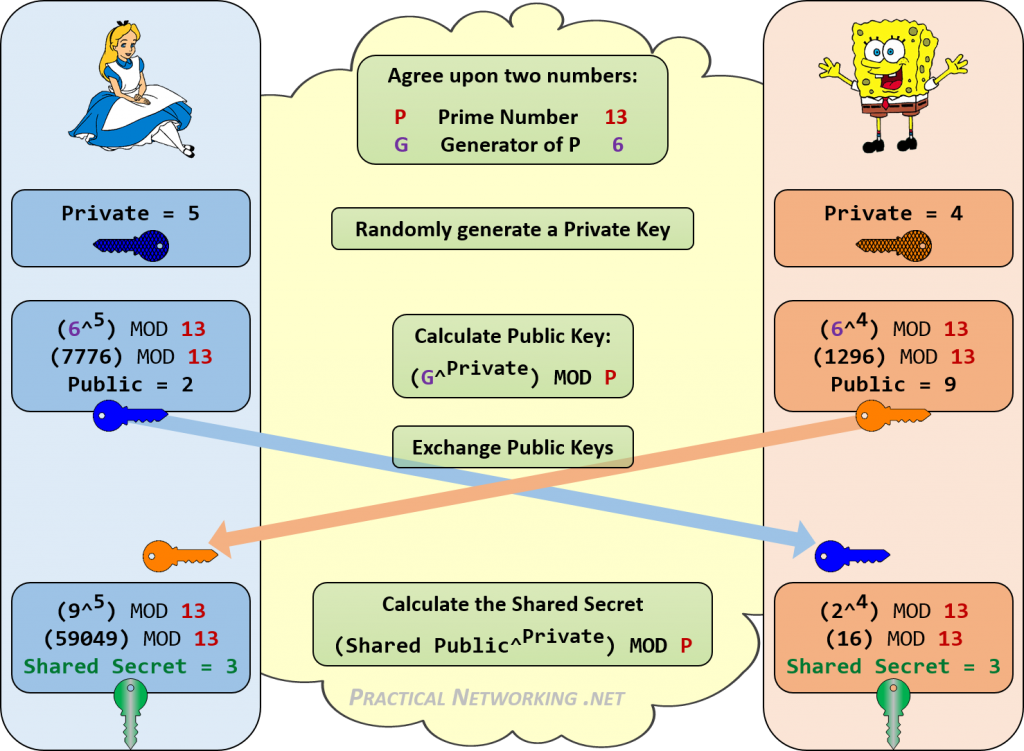
How to securely exchange encryption & decryption keys over a public communication network? | by Dasitha Abeysinghe | Medium
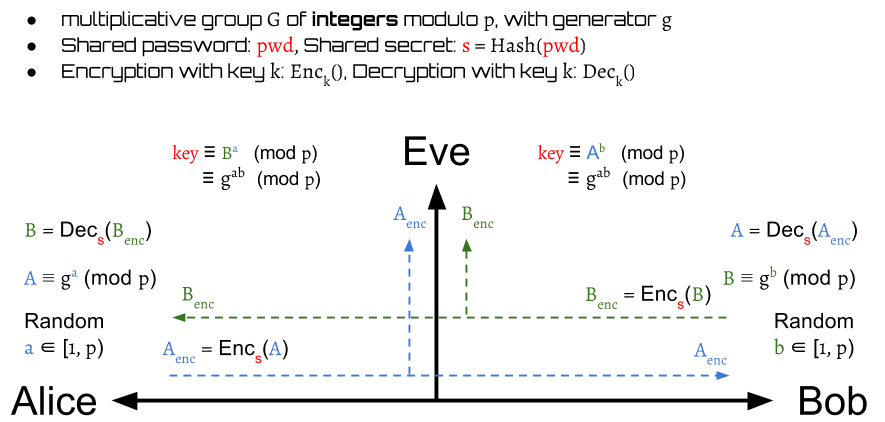
GitHub - pubnub/secure-key-exchange: Babel - Encrypted Self Destructing Messaging with Asymmetric Key Exchange Public-Private Crypto.
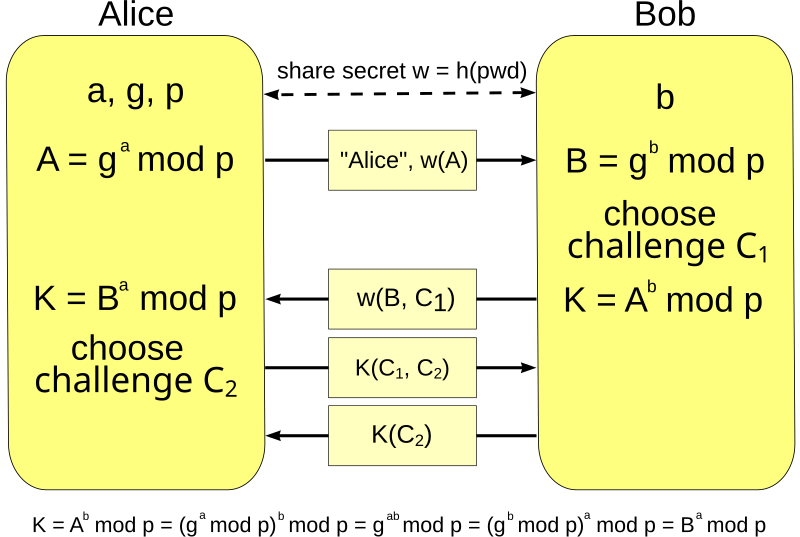
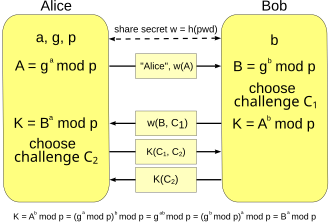
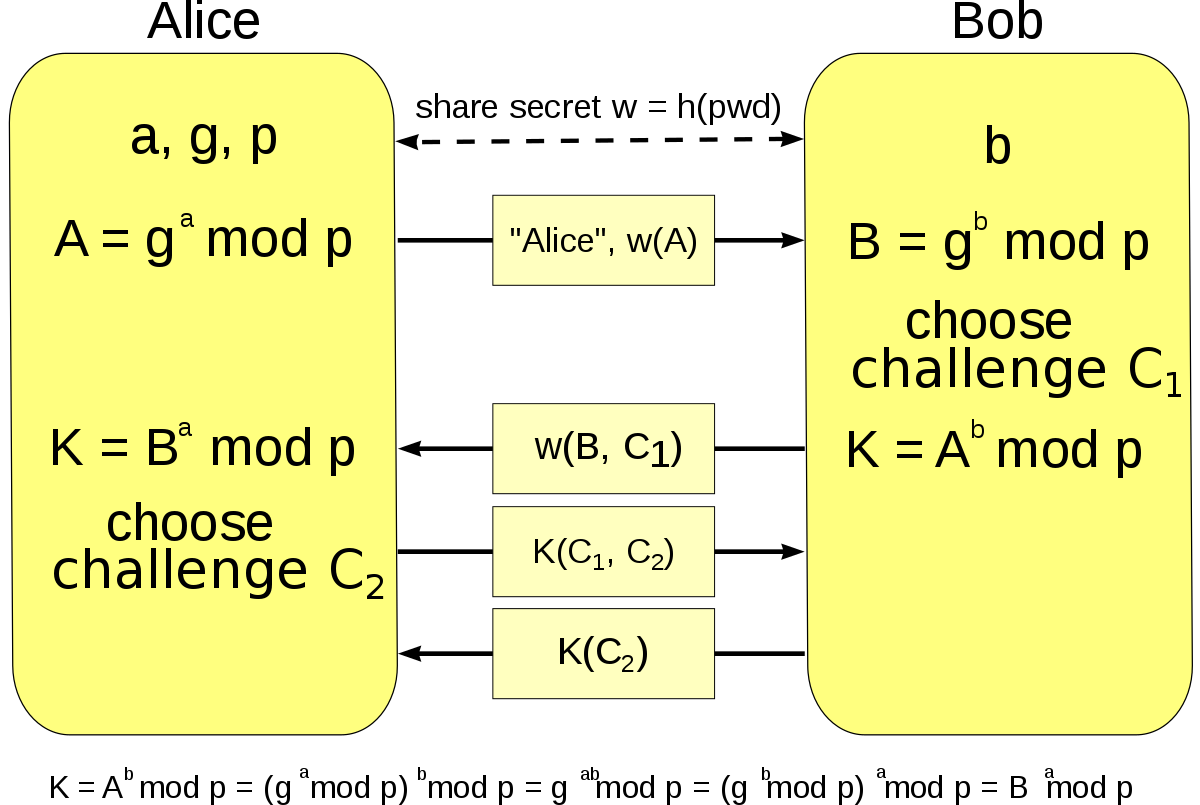
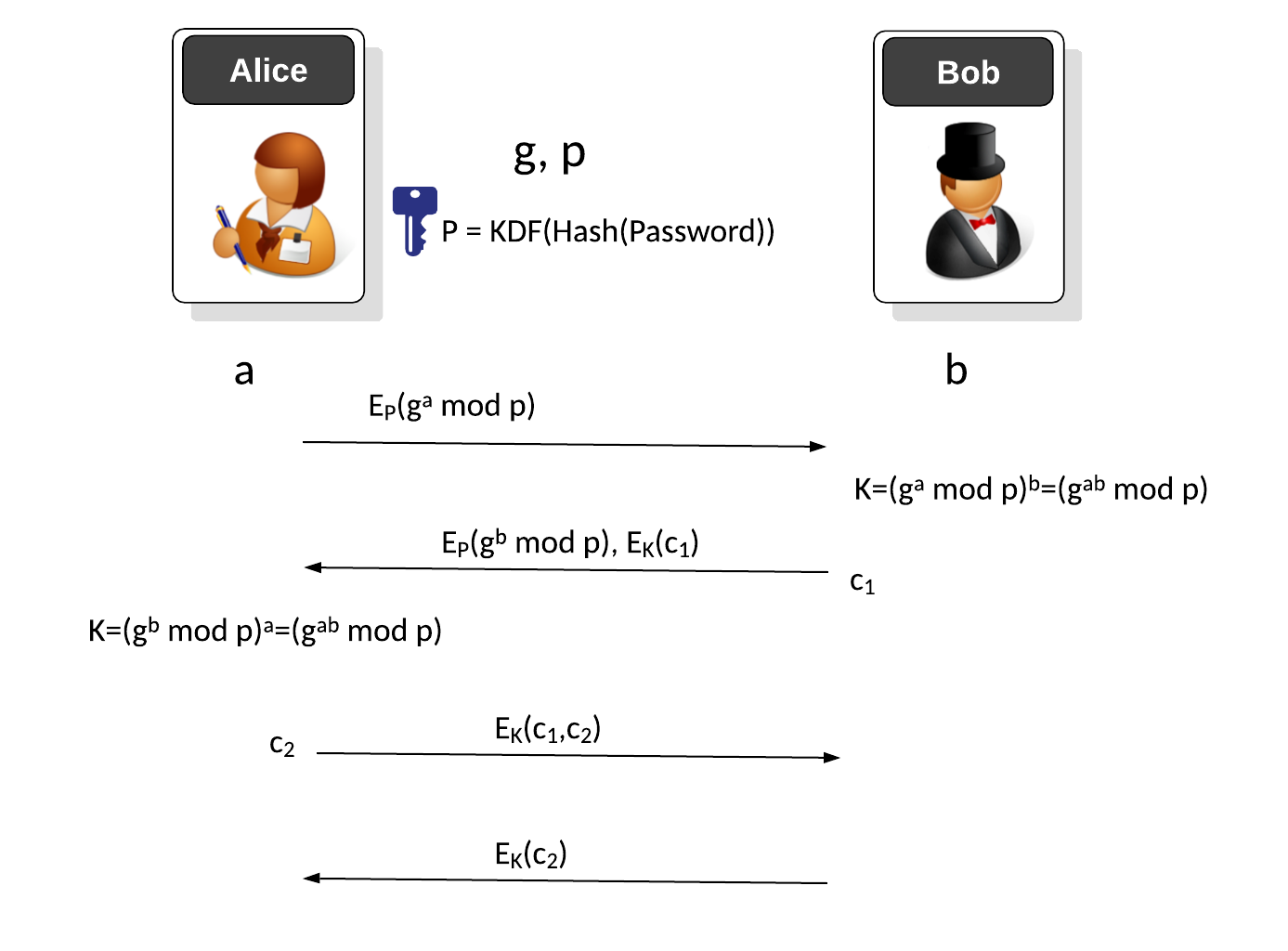
![PDF] Augmented Password-Authenticated Key Exchange for Transport Layer Security (TLS) | Semantic Scholar PDF] Augmented Password-Authenticated Key Exchange for Transport Layer Security (TLS) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f4b2215d29f891e2586594f2f0cb083c03ead717/7-Figure1-1.png)