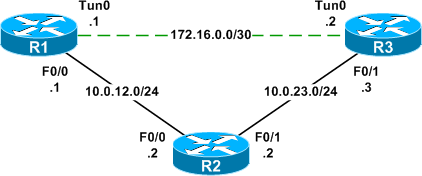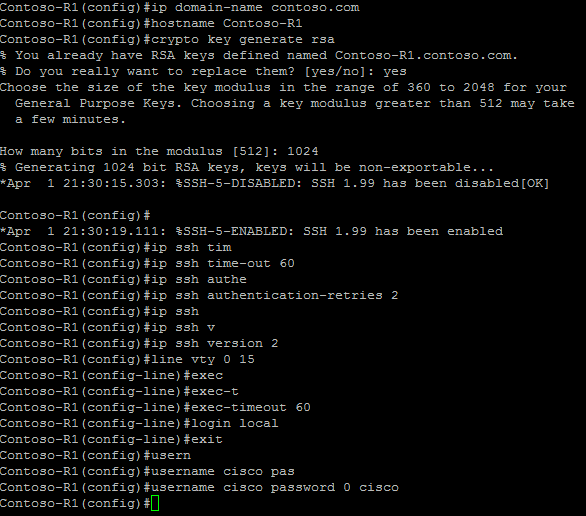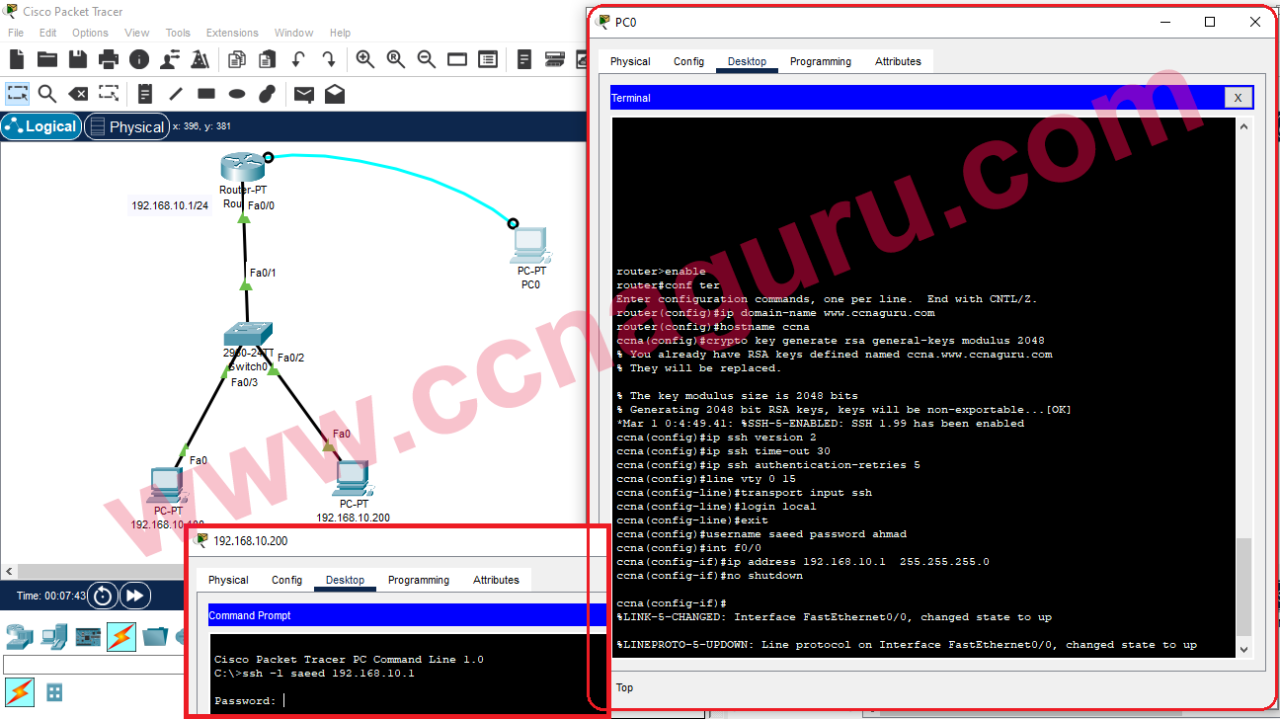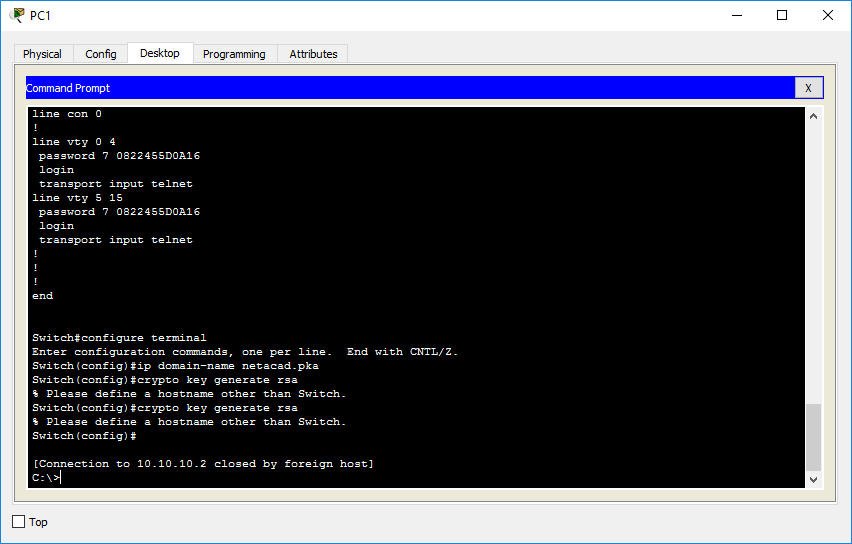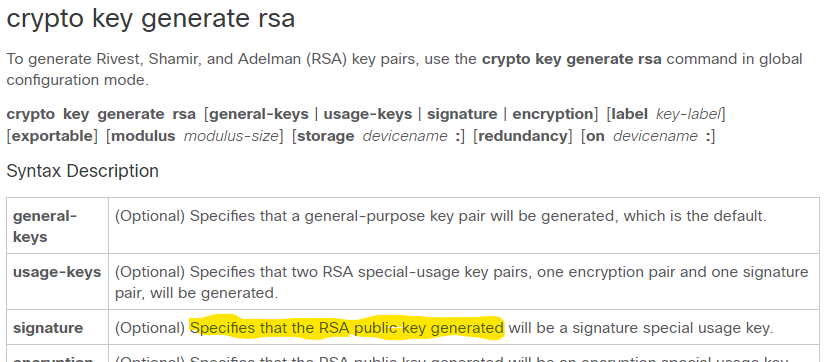
PI 3.2 Erstellen einer benutzerdefinierten CLI-Vorlage mit einer Leitung und mehreren Befehlszeilen - Cisco
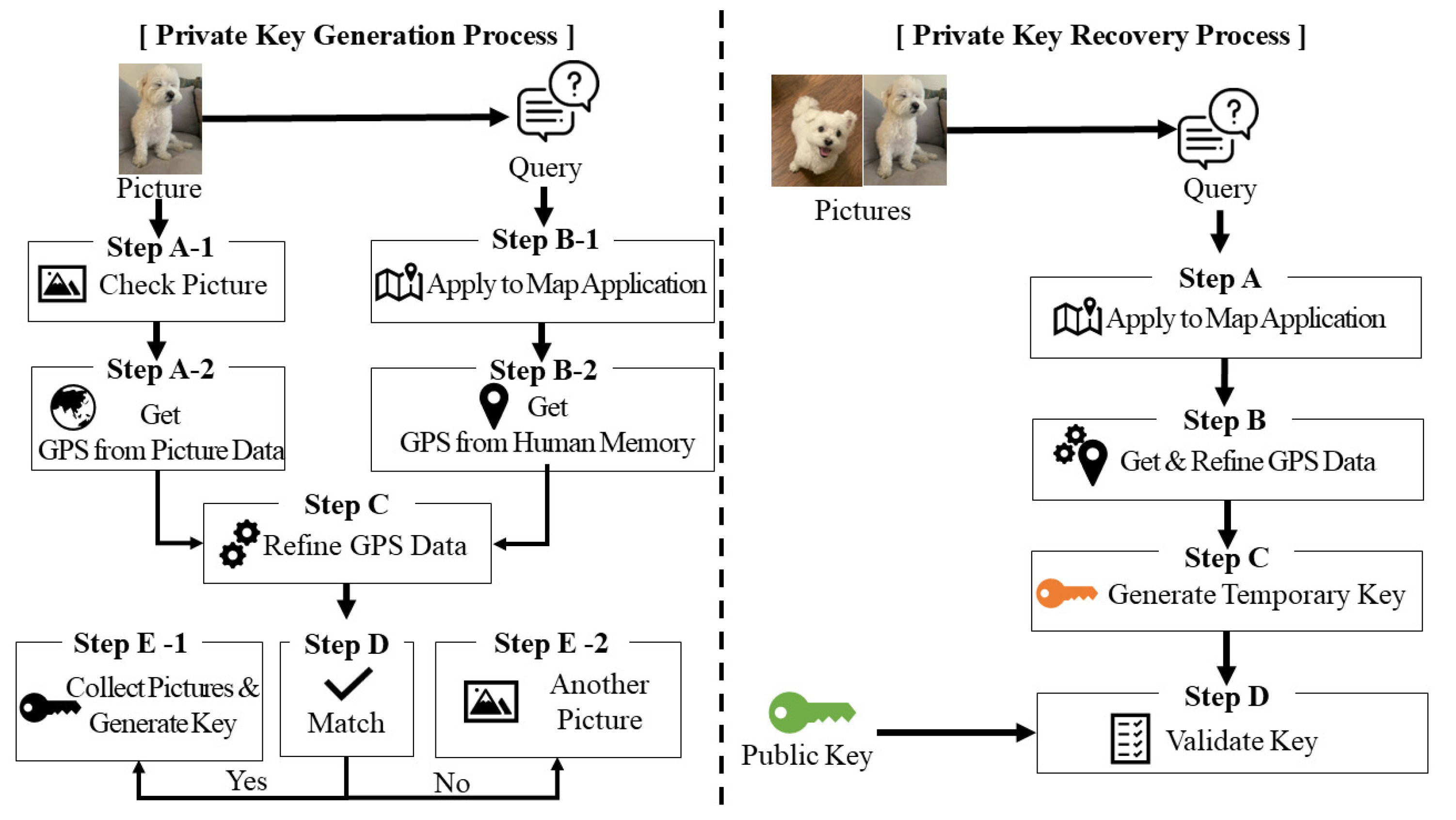
Mathematics | Free Full-Text | Reminisce: Blockchain Private Key Generation and Recovery Using Distinctive Pictures-Based Personal Memory
![Security - Configuring Certificate Authorities and Digital Certificates [Cisco MDS 9000 NX-OS and SAN-OS Software] - Cisco Systems Security - Configuring Certificate Authorities and Digital Certificates [Cisco MDS 9000 NX-OS and SAN-OS Software] - Cisco Systems](https://www.cisco.com/en/US/i/100001-200000/140001-150000/144001-145000/144788.jpg)