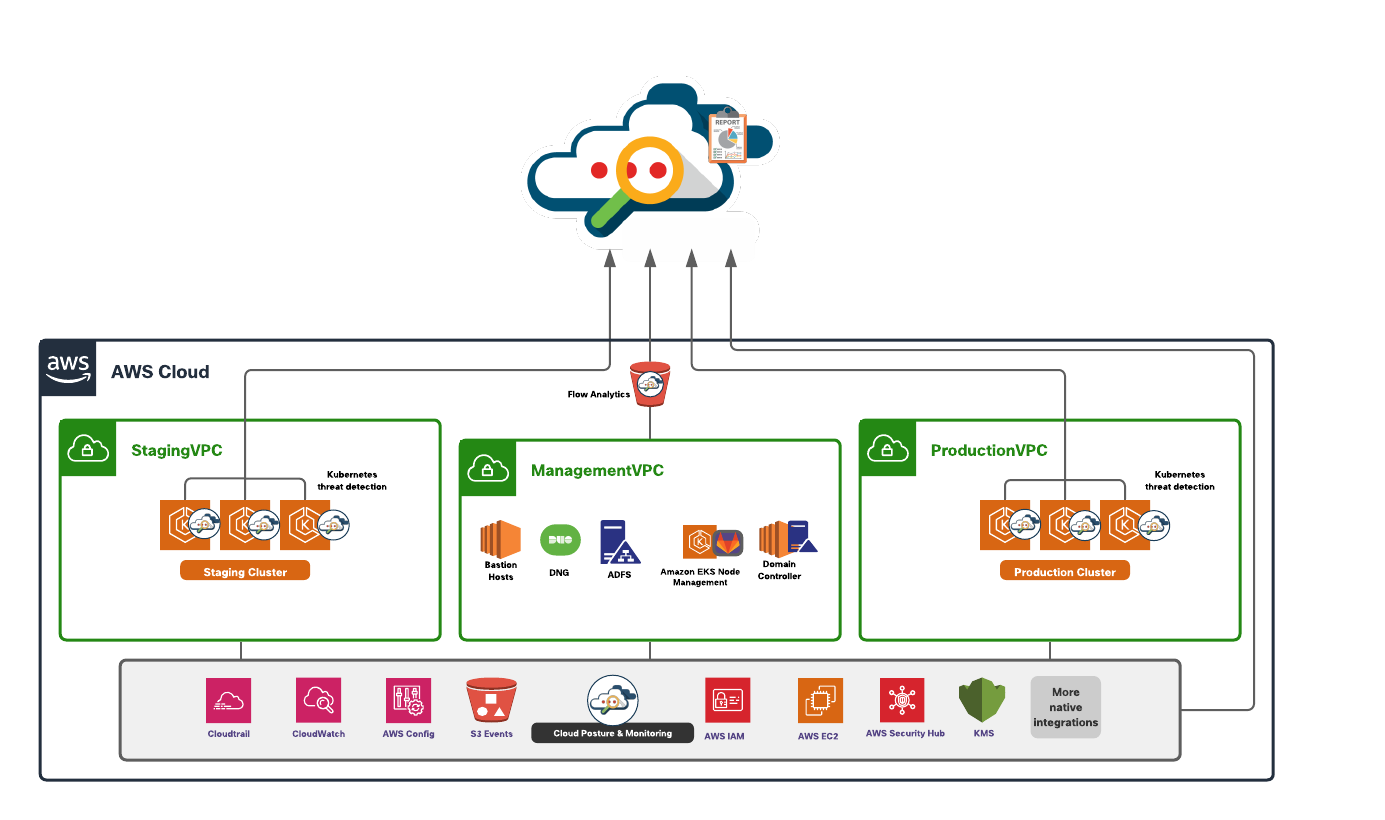
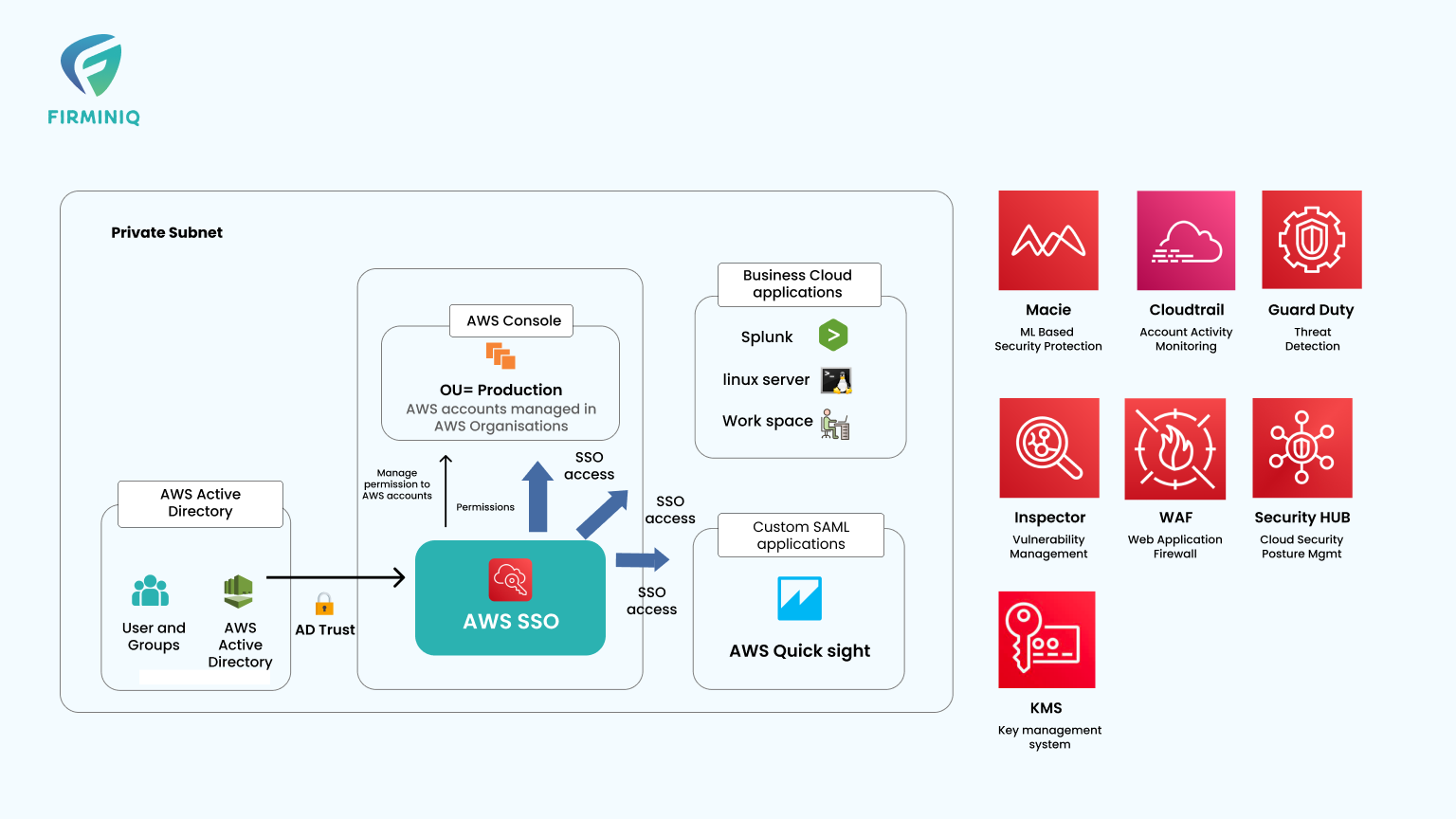
Collect and respond to security events: Aligning to the MovieLabs Common Security Architecture for Production (CSAP) | AWS for M&E Blog

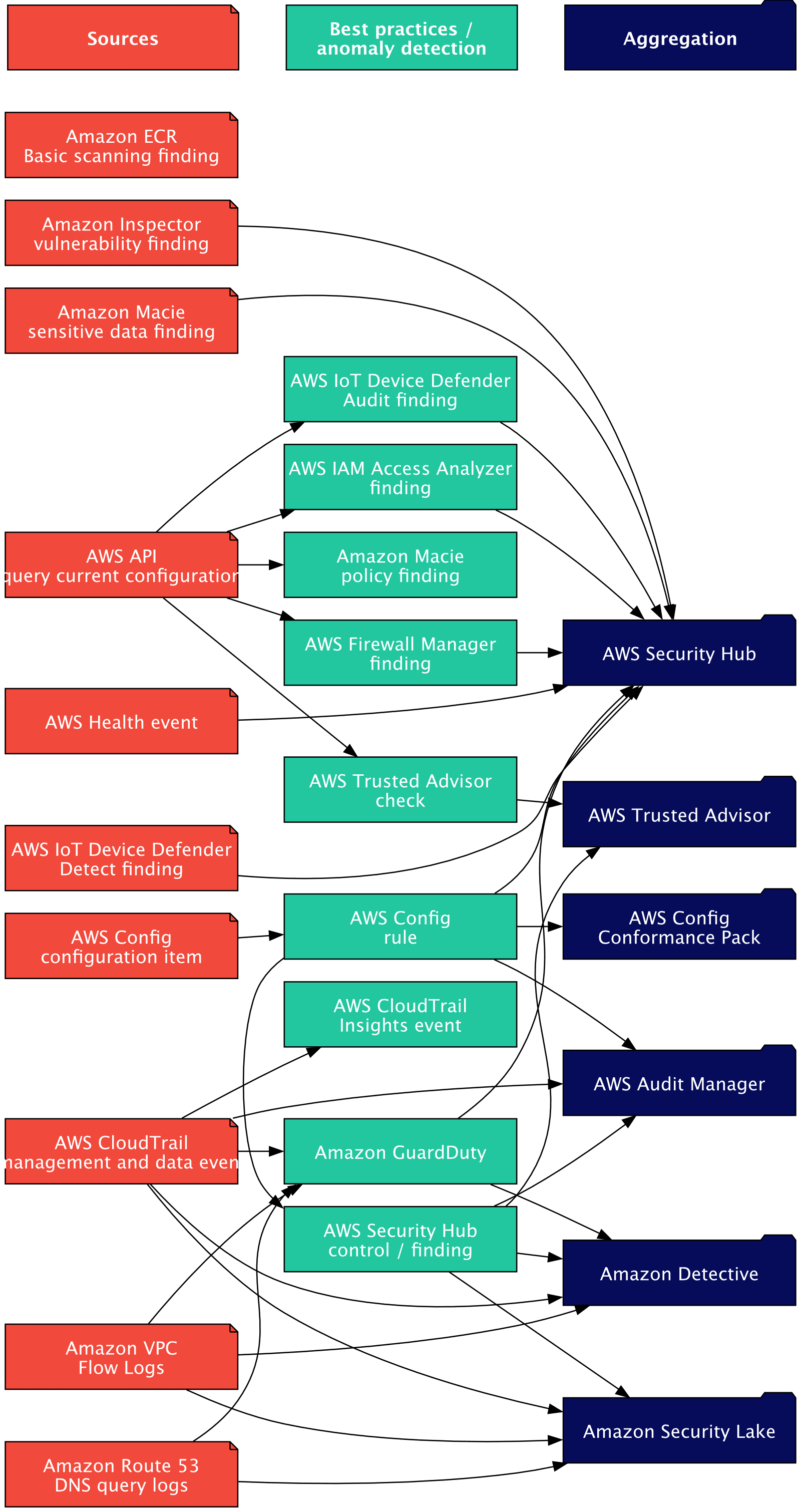
Configure logging and monitoring for security events in your AWS IoT environment - AWS Prescriptive Guidance

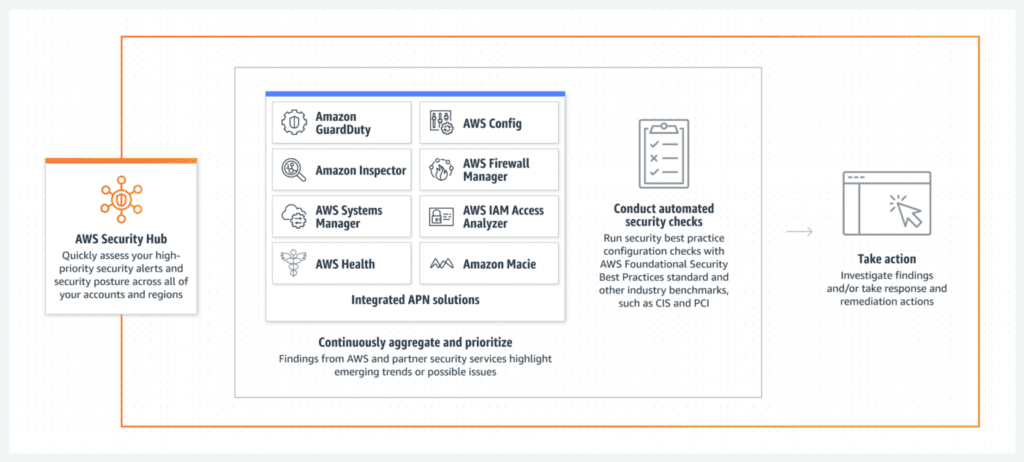
Alerting, monitoring, and reporting for PCI-DSS awareness with Amazon Elasticsearch Service and AWS Lambda | AWS Security Blog