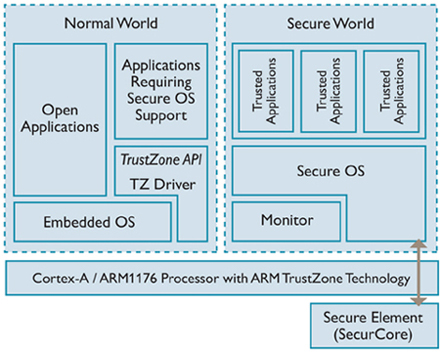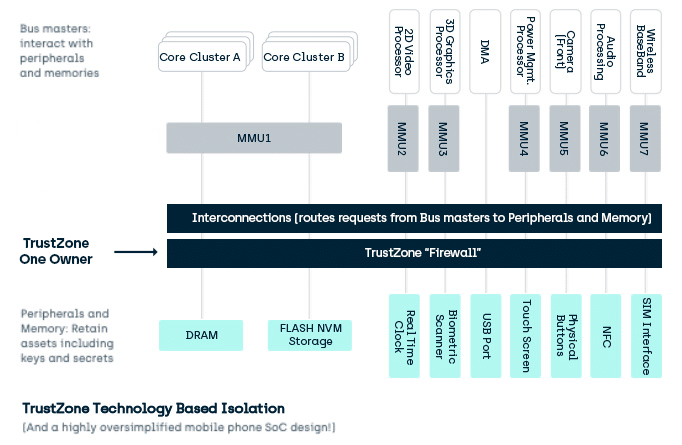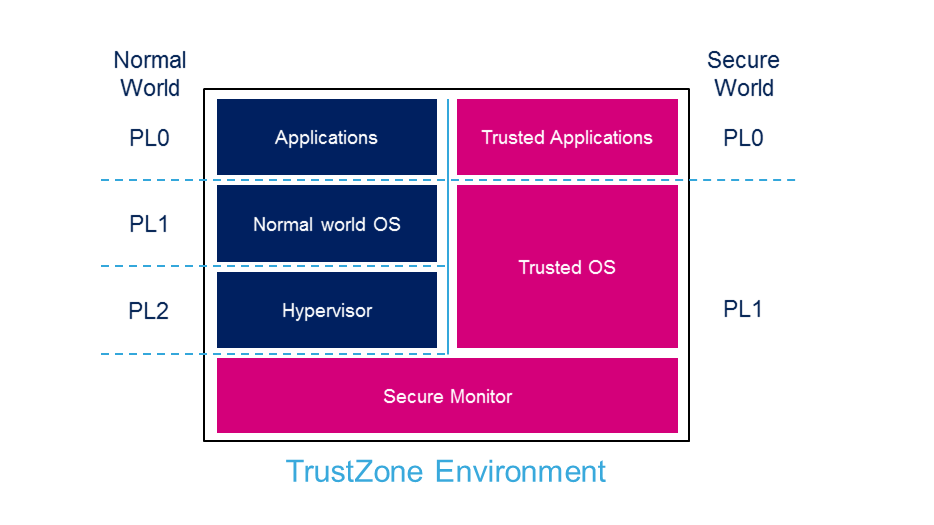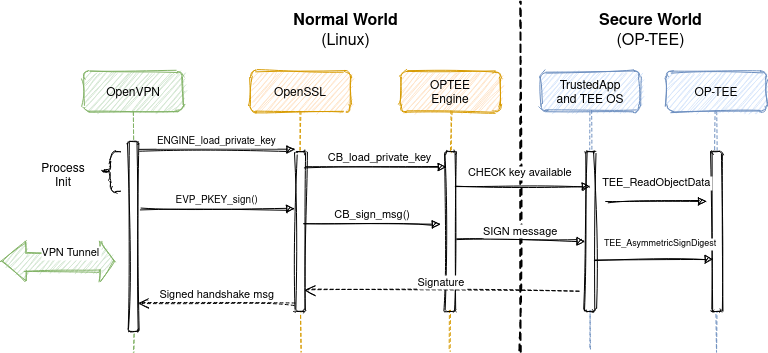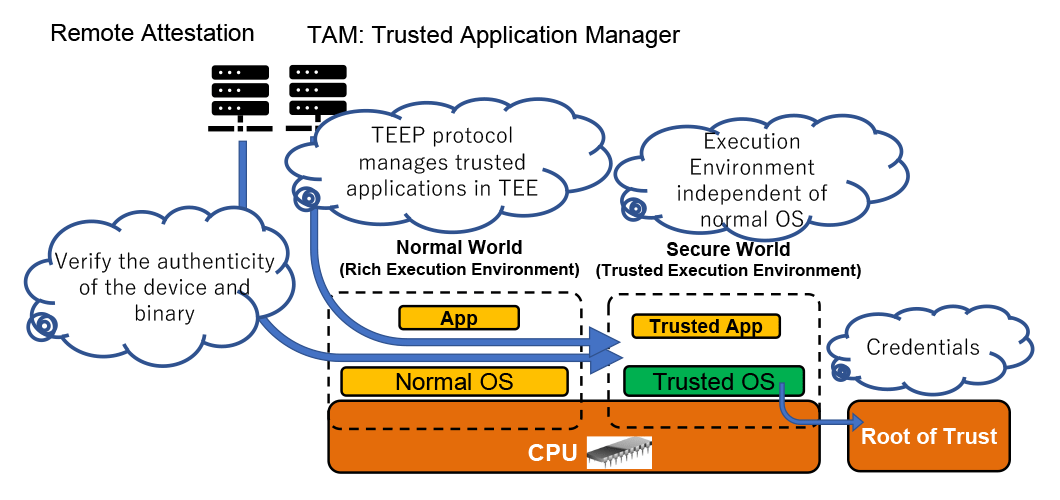
TEE (Trusted Execution Environment) and its supporting technologies | Cryptography Platform Research Team | Cyber Physical Security Research Center - AIST
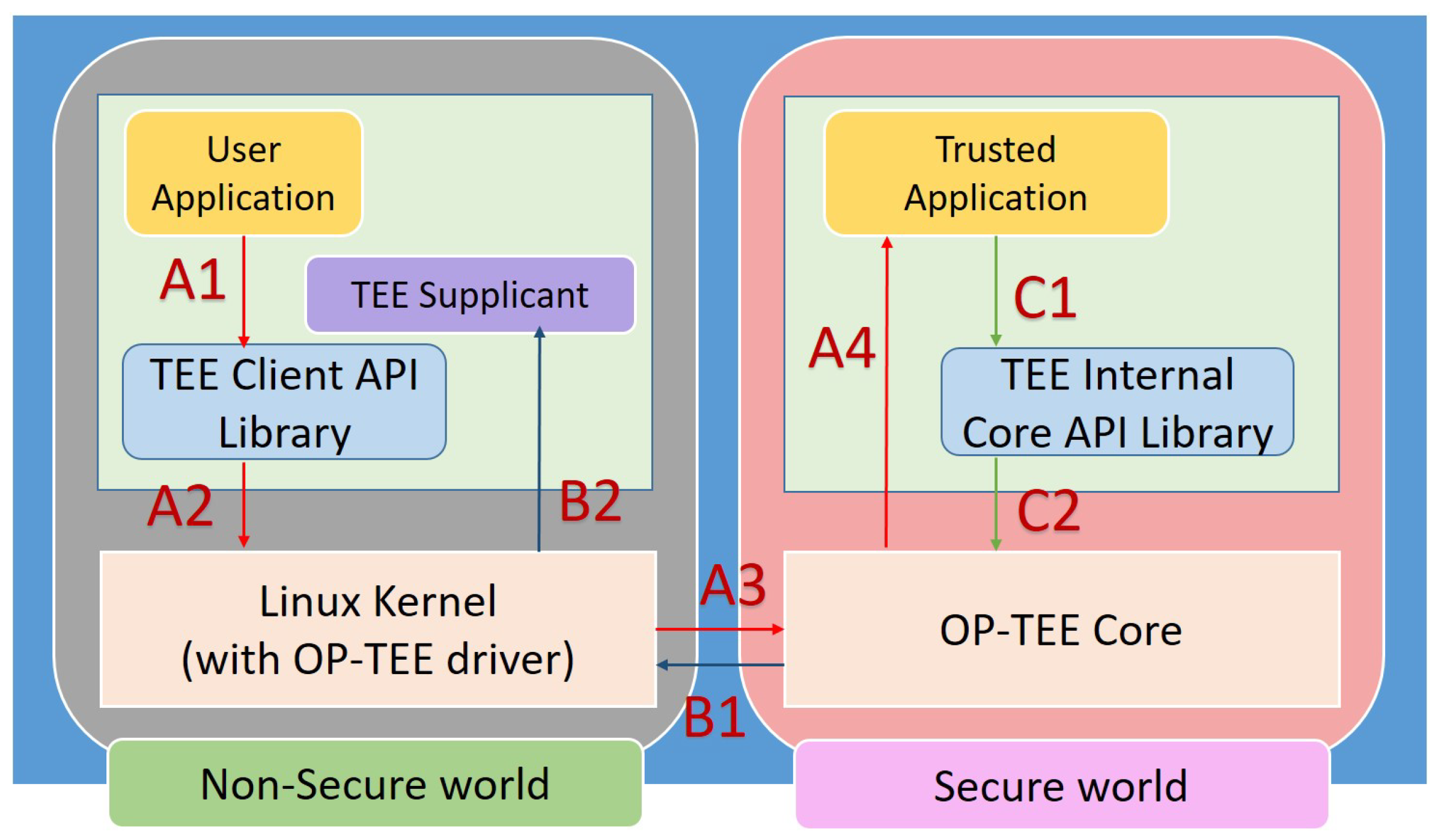
![shows libraries and utilities for running ARM TrustZone [32]-[34]. ARM... | Download Scientific Diagram shows libraries and utilities for running ARM TrustZone [32]-[34]. ARM... | Download Scientific Diagram](https://www.researchgate.net/publication/341065681/figure/fig1/AS:886202358042624@1588298515144/shows-libraries-and-utilities-for-running-ARM-TrustZone-32-34-ARM-TrustZone-consists.png)
shows libraries and utilities for running ARM TrustZone [32]-[34]. ARM... | Download Scientific Diagram
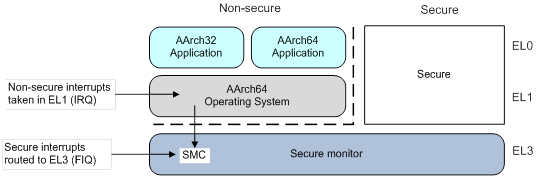
Sustainability | Free Full-Text | STBEAT: Software Update on Trusted Environment Based on ARM TrustZone

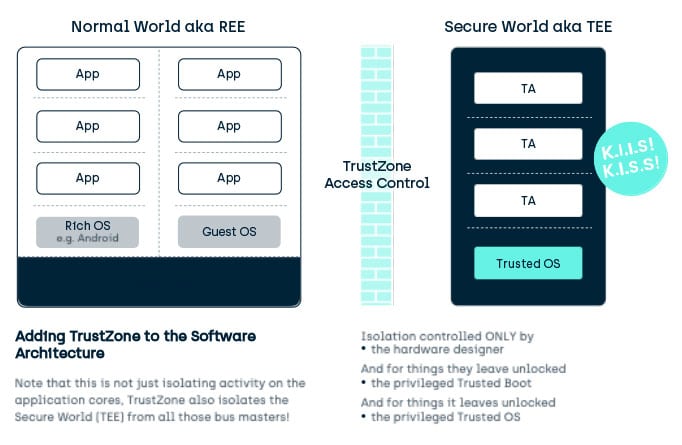
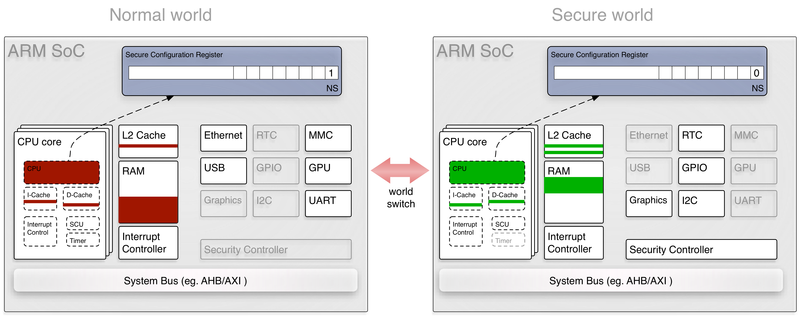
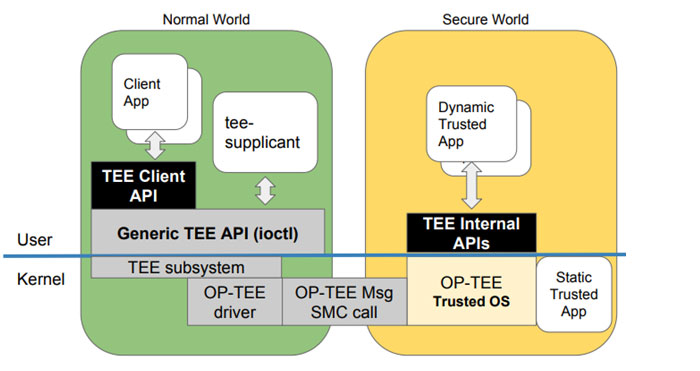

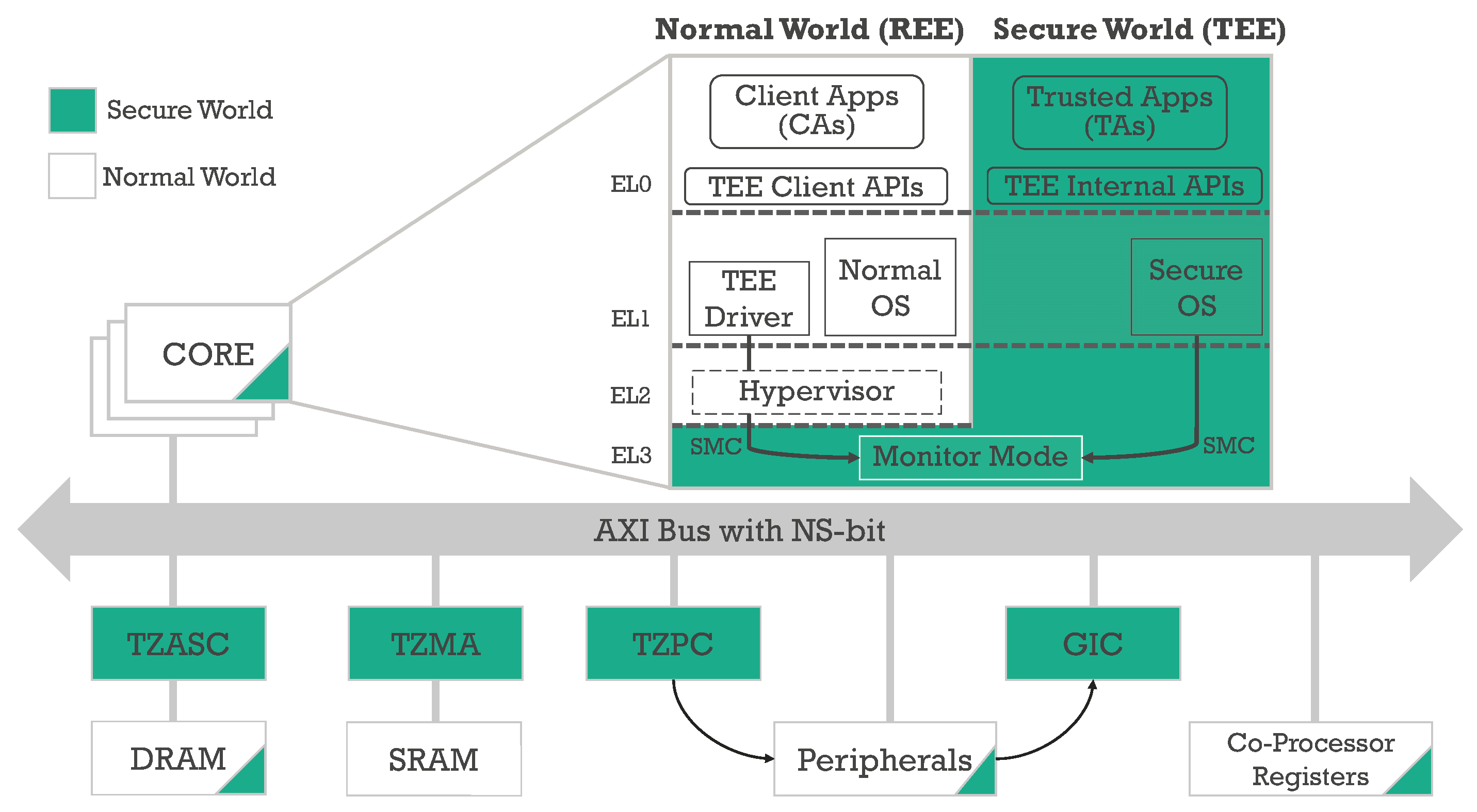
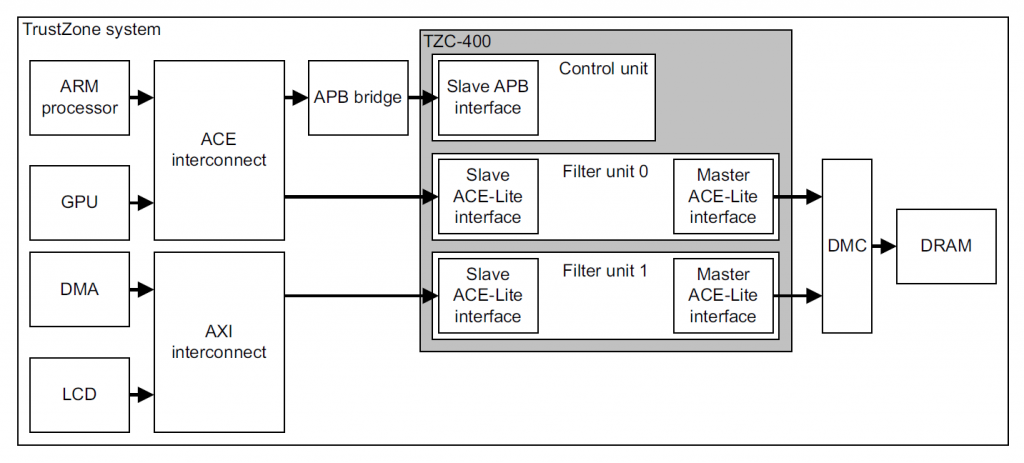

![PDF] vTZ: Virtualizing ARM TrustZone | Semantic Scholar PDF] vTZ: Virtualizing ARM TrustZone | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/bad6552f0b3e533194c9c1d8a26a5fd470b1b24d/6-Figure2-1.png)




![PDF] Demystifying Arm TrustZone | Semantic Scholar PDF] Demystifying Arm TrustZone | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6ae73b993d091105f3f99f90b3fcc39045aae783/4-Figure1-1.png)